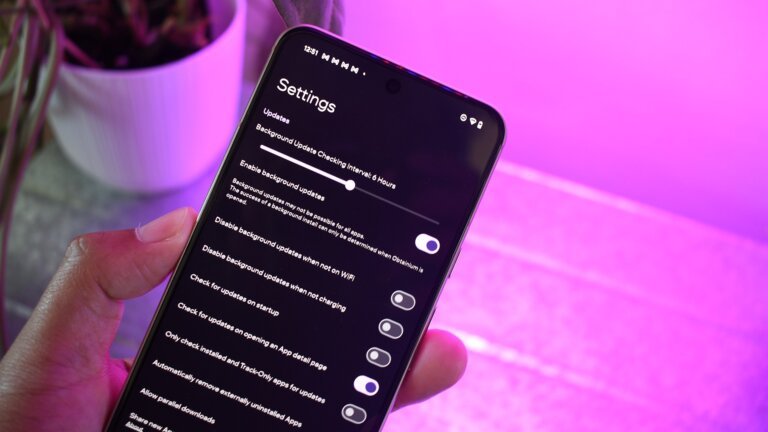
Obtanium is an app that allows users to install, update, and manage apps from various platforms like F-Droid, GitHub, and the vivo Store.
Breezy Weather is a weather app designed for Google Pixel users, providing comprehensive weather details and integrating with the Pixel Launcher.
Nobook is a wrapper for Facebook Lite that offers ad-blocking features and customization options for a streamlined experience.
Forkyz aggregates crossword puzzles from various sources, providing entertainment for crossword enthusiasts.
Suntimes is an older app that tracks daylight hours, useful for planning outdoor activities.
Canta helps users remove unwanted system-level applications, allowing for device decluttering.
Shizuku grants system-level access to other applications, enhancing their functionality, particularly for power users.
Kvaesitso is a launcher with infinite vertical scrolling and extensive widget support, offering customization options.
Tubular is a lightweight alternative to the stock YouTube app, blocking sponsor segments and reintegrating the dislike counter.
Aurora Store allows users to access Play Store apps without needing a Google account, appealing to privacy-conscious users.
ColorBlendr enables users to customize their device's theme colors for a personalized look.
Fennec is a privacy-focused browser based on Mozilla Firefox, eliminating trackers and supporting add-ons.
SmartSpacer enhances the At A Glance widget by overlaying information from third-party apps.
Exodus provides insights into installed apps, revealing trackers and permissions for privacy-conscious users.
OSS Document Scanner is an open-source app that combines OCR capabilities with visual editing features for document management.