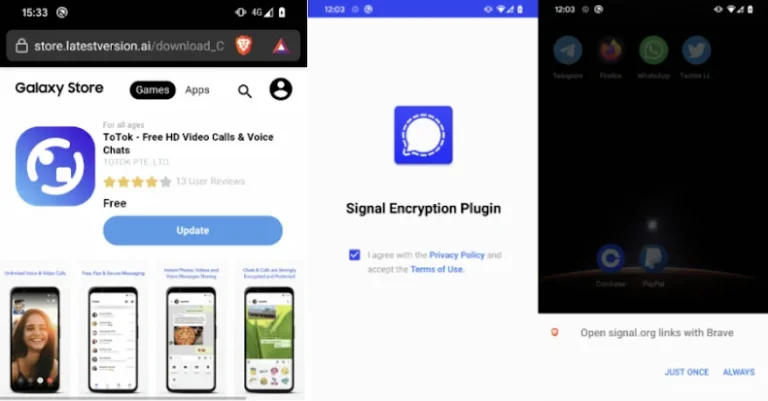
Android users are facing sophisticated spyware threats, specifically two strains known as ProSpy and ToSpy, which disguise themselves as legitimate applications like updates for Signal and ToTok. These malware types evade detection and steal sensitive information such as messages, contacts, and location data by requesting innocuous permissions. In 2025, spyware detections increased by 147%, with attackers mimicking financial tools and system updates. Google plans to implement a policy requiring app registration to verified developers in 2026 to combat these threats. Experts recommend downloading apps only from the Google Play Store, enabling Play Protect, and using reputable antivirus software. Vigilance against unofficial sources is crucial for protecting personal and professional data. New threats like ClayRat are emerging, further complicating the security landscape.