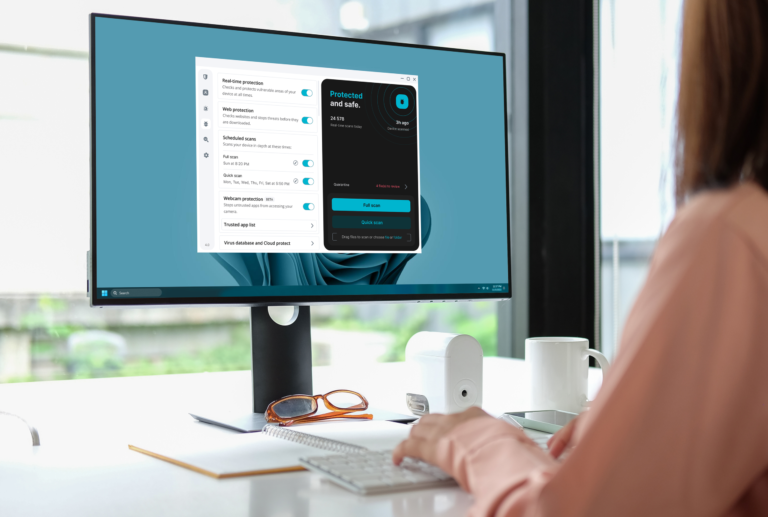
In 2026, consumers are increasingly opting for bundled cybersecurity solutions due to the confusion caused by separate antivirus tools, VPN subscriptions, and privacy utilities. XShield, operated by Xshield Technologies AG, is a subscription-based digital privacy protection suite that consolidates various security functions, including antivirus, secure VPN, cyber privacy tools, anti-ransomware defenses, dark web monitoring, and mobile security. It is compatible with iOS, Android, Windows, and macOS devices, offering unlimited device coverage under one subscription. The setup process takes about two minutes, and customer support is available 24/7 via live chat, with email and phone assistance during business hours. Subscriptions automatically renew unless canceled.
XShield offers two subscription tiers: a monthly plan at .99 per month and a yearly plan at .99 per year, which includes two months free. Both plans provide full access to the security suite. A 30-day money-back guarantee is available for first-time purchases, but it does not cover subscription renewals or third-party purchases. Consumers are advised to seek independent testing results, clarify the meaning of "unlimited devices," understand auto-renewal terms, examine VPN specifications, and consider mobile platform security differences before subscribing.