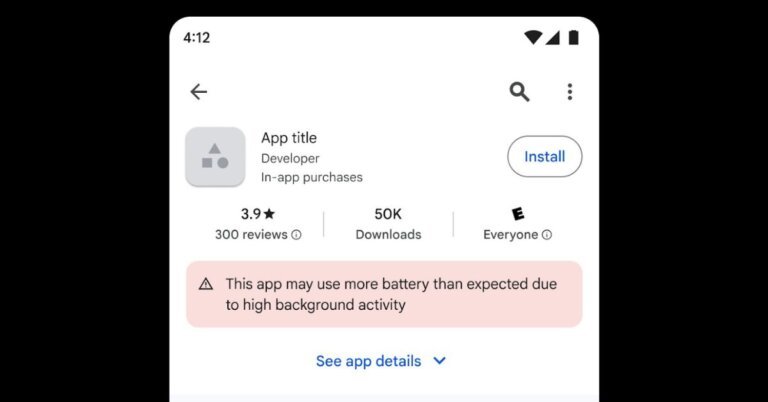
The Galaxy S26 Ultra has raised concerns about battery performance, leading users to seek solutions for extending battery life. In response, Google is working to simplify the identification of applications that drain battery resources, particularly those using the "wake lock" feature, which keeps the CPU active when the screen is off. Google plans to implement technical measures to reduce wake lock overuse and introduce disclaimers for apps that frequently exceed the "Excessive Partial Wake Lock" threshold. If issues persist, Google may limit the visibility of such apps in the Play Store. This initiative is part of a broader strategy to improve battery efficiency across Android devices, including a prototype warning for users about battery-draining apps. Google is also collaborating with developers to optimize apps that rely on background processes, as seen in its partnership with WHOOP to enhance battery efficiency in its applications.