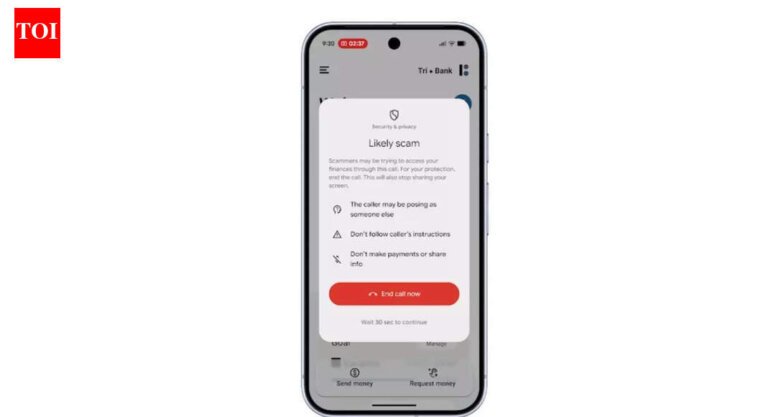
The holiday season sees increased online activity, making it a prime time for cybercriminals to exploit vulnerabilities. IT teams are often overwhelmed, and employees may be distracted, leading to a higher risk of phishing scams, ransomware attacks, and data breaches. Strategies to enhance digital security include using strong, unique passwords of at least 16 characters, enabling multi-factor authentication (MFA), being cautious with unfamiliar links, keeping devices updated with software patches, installing antivirus software, using secure networks (preferably with a VPN), enabling firewalls and endpoint protection, limiting user privileges, encrypting and backing up data, and reporting suspicious activity to relevant authorities.