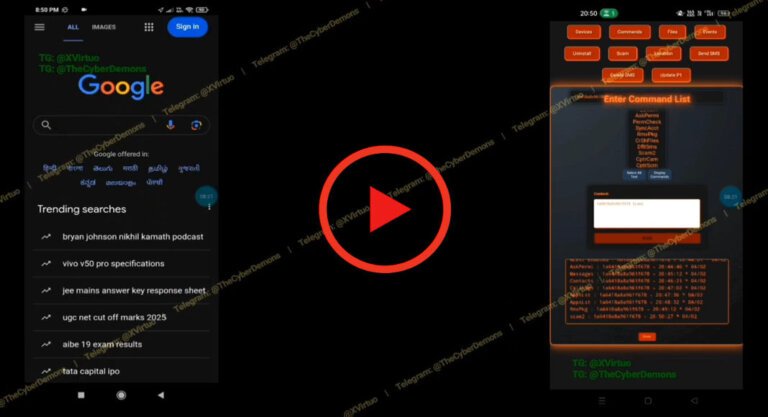
Cybersecurity researchers have identified a new Android trojan named Massiv, designed for device takeover attacks targeting financial theft. It disguises itself as IPTV applications and poses risks to mobile banking users by allowing operators to remotely control infected devices for fraudulent transactions. The malware was first detected in campaigns targeting users in Portugal and Greece, with features including screen streaming, keylogging, SMS interception, and fake overlays for credential theft. One campaign specifically targeted the gov.pt application to deceive users into providing sensitive information. Massiv can execute various malicious actions, such as altering device settings, sending device information, and downloading malicious files. It is distributed through dropper applications that mimic IPTV services, often via SMS phishing. The malware operates in the background while the dropper appears as a legitimate app. Recent campaigns have focused on regions like Spain, Portugal, France, and Turkey, indicating a growing threat landscape. The operators of Massiv are developing it further, suggesting intentions to offer it as a Malware-as-a-Service.