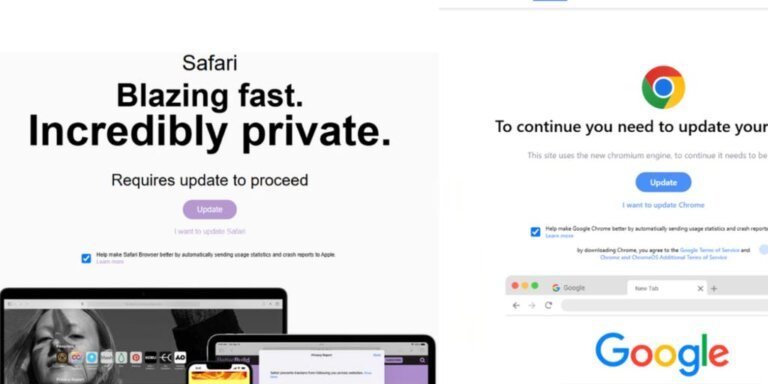
Recent developments indicate that Mac users are facing an escalating threat from malware designed for macOS systems, particularly with the emergence of a strain called FrigidStealer. This malware spreads through deceptive browser update prompts on compromised websites, leading users to download a malicious DMG file that seeks elevated privileges to steal sensitive information. Cybersecurity firm Proofpoint has traced the operations of FrigidStealer to two threat actors: TA2726, a traffic distribution service provider, and TA2727, which delivers the malware. This campaign also targets Windows and Android devices, indicating a multi-platform strategy. Additionally, the rise of infostealer malware has compromised approximately 330 million credentials in 2024, with around 3.9 billion credentials circulating from infostealer logs. Users are advised to adopt protective measures, including being cautious of fake software updates, enabling two-factor authentication, using password managers, and exercising caution with downloads and links.