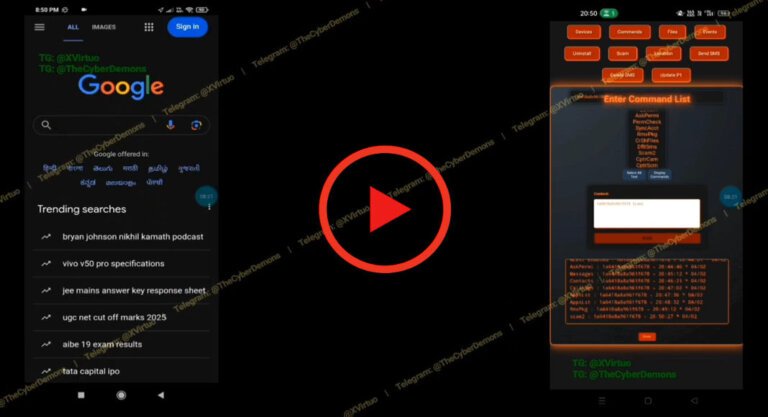
A new Android Remote Access Trojan (RAT) has appeared on GitHub, described as fully undetectable and capable of bypassing advanced permission and background process restrictions in customized Chinese ROMs like MIUI and EMUI. This malware utilizes a multi-layer dropper to integrate its payload within legitimate applications, allowing it to overcome autostart restrictions and battery optimization features. Upon installation, it escalates privileges to gain comprehensive access to the device, using AES-128-CBC encryption for command-and-control communication to evade detection.
The RAT can record and delete call logs, intercept voice calls, manipulate SMS messages, and capture keystrokes through a keylogger. It also has capabilities for live screen captures, camera access, audio and video recording, and clipboard hijacking. Additionally, it can encrypt files and lock the device, demanding a ransom for access. The malware employs social engineering tactics, such as spoofed notifications and phishing prompts, to facilitate credential theft.
Its persistence mechanisms allow it to operate with minimal resource usage, making detection difficult. The attacker interface is web-based, enabling control from any standard browser without specialized infrastructure. The public release of this RAT raises concerns about the misuse of open-source repositories for distributing malicious tools, prompting calls for stricter oversight on platforms like GitHub.