Bungie conducted a "server slam" for the reboot of Marathon to stress-test its online capabilities ahead of the release on March 5th. Players provided feedback on various aspects, including:
- UI Feedback: Bungie is collecting user input on the user interface and plans to iterate post-launch.
- PC Performance: Issues reported include high CPU usage, low GPU utilization, FPS ceilings around 80-100, and stuttering.
- PvP Frequency: Bungie is investigating player density on maps and welcomes feedback on gameplay experiences.
- Movement and Heat Generation: Discussions about heat generation and momentum are ongoing, with players encouraged to share thoughts on movement mechanics.
- Med and Ammo Economy: Feedback on the economy of medical supplies and ammunition, particularly regarding stack sizes and item effectiveness, is being collected.
- Weasel Error Codes: Players have encountered Weasel error codes related to network disruptions, and Bungie is investigating these issues.
The author expressed mixed feelings about the gameplay experience, noting issues with extraction-shooting mechanics and ammunition shortages, while appreciating the art direction.
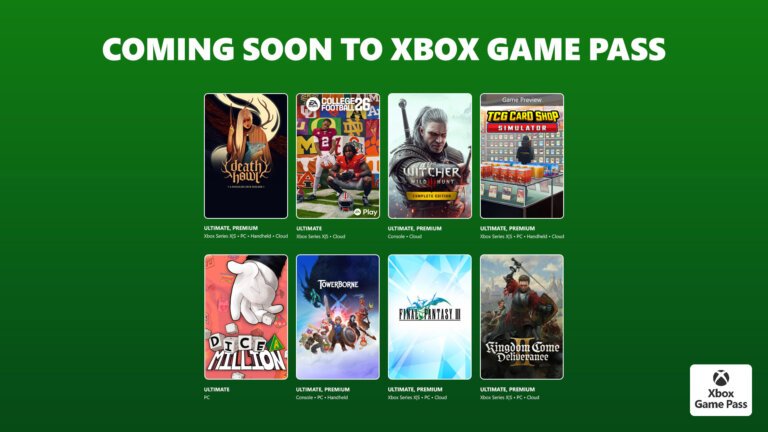
AerialKnight’s DropShot is available on February 17 for Cloud, Xbox Series X|S, Handheld, and PC via Game Pass Ultimate and PC Game Pass. Avatar: Frontiers of Pandora is also available on February 17 for the same platforms, featuring a first-person action-adventure experience. Avowed receives an update on February 17, introducing new playable races, a New Game Plus Mode, and a Photo Mode. Death Howl will launch on February 19 for Cloud, Xbox Series X|S, Handheld, and PC on Game Pass Ultimate and Premium. EA Sports College Football 26 is available on February 19 for Cloud and Xbox Series X|S, allowing players to represent 136 FBS schools. The Witcher 3: Wild Hunt – Complete Edition launches on February 19 for Cloud and Console. TCG Card Shop Simulator enters Game Preview on February 24 for multiple platforms. Dice A Million will be available on PC on February 25 with Xbox Game Pass. Towerborne releases as a complete game on February 26 for Console, Handheld, and PC. Final Fantasy III and Kingdom Come: Deliverance II are set for March 3 on multiple platforms. Menace entered Game Preview on February 5 for PC, and Diablo II: Resurrected was released on February 11 for Console and PC. Overwatch: Season 1: Conquest began on February 10, introducing new heroes. Microsoft Mahjong will feature in-game benefits on February 24 for PC. Titles leaving Game Pass on February 28 include Monster Train, Expeditions: A MudRunner Game, Injustice 2, and Middle Earth: Shadow of War.