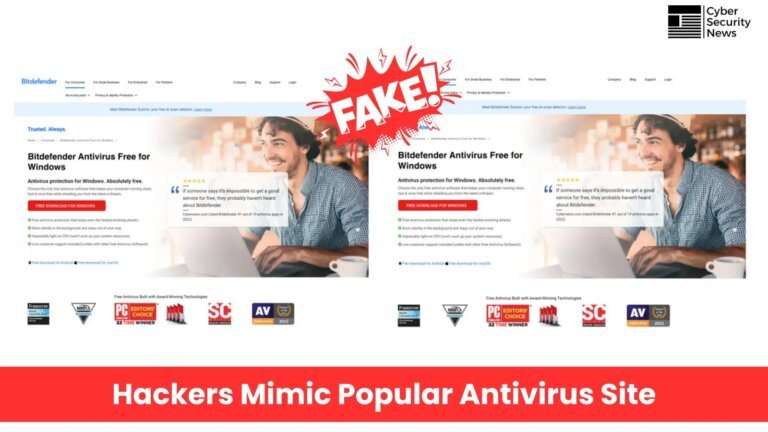
Cybercriminals are executing a sophisticated malware campaign through a counterfeit Bitdefender antivirus website, specifically the domain “bitdefender-download[.]co,” which mimics the legitimate site. This fraudulent site distributes three types of malware: VenomRAT, StormKitty, and SilentTrinity, aimed at stealing financial data and maintaining persistent access to victims’ computers.
When users click the “Download For Windows” button, they inadvertently download a ZIP file containing these malicious programs. VenomRAT acts as a remote access tool, allowing attackers to steal files, cryptocurrency wallets, and browser data, including credit card information. StormKitty quickly harvests sensitive credentials, while SilentTrinity provides stealthy long-term access for further exploitation.
The fake Bitdefender site is linked to other malicious domains impersonating banks, indicating a coordinated phishing operation. The attackers utilize the same command and control infrastructure, with the IP address 67.217.228.160:4449 identified as a connection point. Bitdefender is working to take down the fraudulent site, and Google Chrome has begun flagging the link as malicious. Security experts recommend verifying website authenticity and downloading software only from official sources.