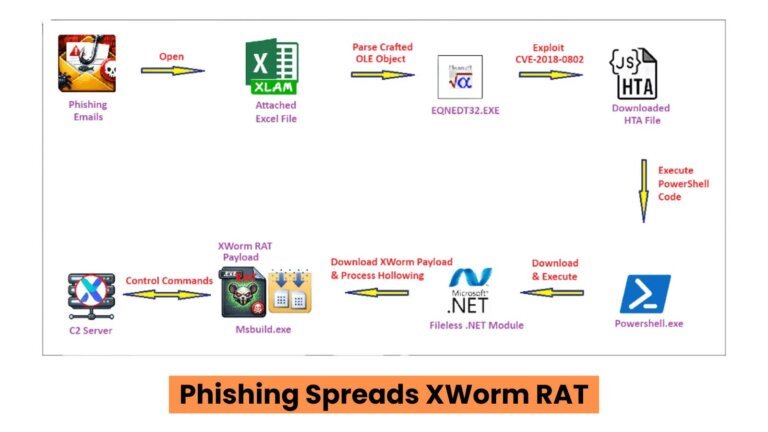
A cyber-espionage campaign is utilizing the XWorm Remote Access Trojan (RAT) to infiltrate systems via phishing emails and a Microsoft Office vulnerability (CVE-2018-0802). XWorm, first detected in 2022, allows attackers remote control over infected computers for surveillance and data theft. The campaign uses business-oriented phishing emails with malicious Excel attachments that exploit the vulnerability to execute a fileless attack. The malware connects to a command-and-control server, encrypting communications and transmitting system details. XWorm features a plugin architecture with over 50 modules for various malicious activities, including credential theft and DDoS attacks. Security experts highlight the ongoing risk of legacy software vulnerabilities and recommend patching outdated components.