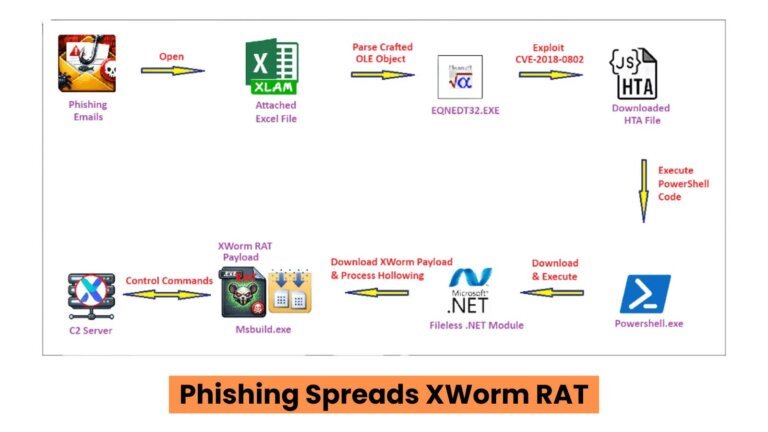
Malware is malicious software designed to disrupt normal system operations, often infiltrating devices through activities like web browsing or opening documents. In 2023, SonicWall Capture Labs reported over 6 billion malware attacks, an 11% increase from the previous year. Common types of malware include viruses, worms, Trojans, spyware, adware, ransomware, fileless malware, and bots. Malware spreads through email attachments, phishing links, compromised websites, fake apps, and removable media. Its effects can include performance issues, data theft, and financial damage. Signs of malware presence include sluggish performance, unexpected crashes, and unauthorized changes. Recommended actions if malware is suspected include disconnecting the device, running a malware scan, and changing passwords. Preventative measures include using security software, practicing safe browsing, keeping software updated, and building security awareness.