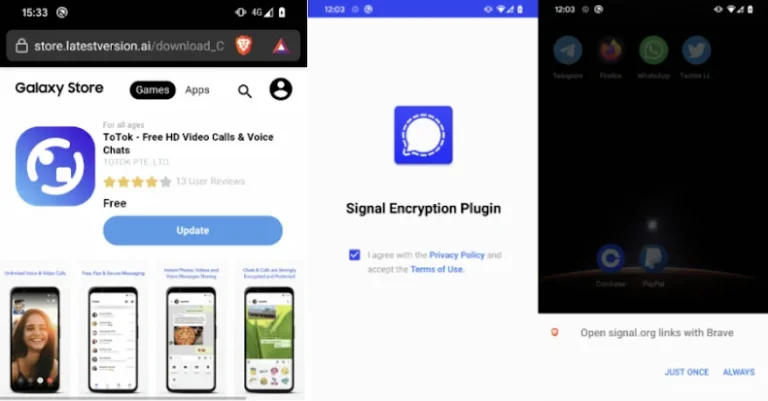
DroidLock is a newly identified ransomware targeting Android users in Europe, capable of locking users out of their devices and demanding ransom for access or threatening permanent data deletion. It spreads through deceptive websites promoting counterfeit applications and gains access to devices by monitoring user passcodes. Victims report ransom demands displayed on their screens, often accompanied by a countdown timer. The ransomware employs phishing tactics to lure users into downloading harmful software, which can lock screens, obtain app lock credentials, exploit device administrator privileges, capture images, and silence devices. While it has not yet reached the UK, experts advise users to download applications only from official sources like the Google Play Store and to verify developer credentials for third-party software.