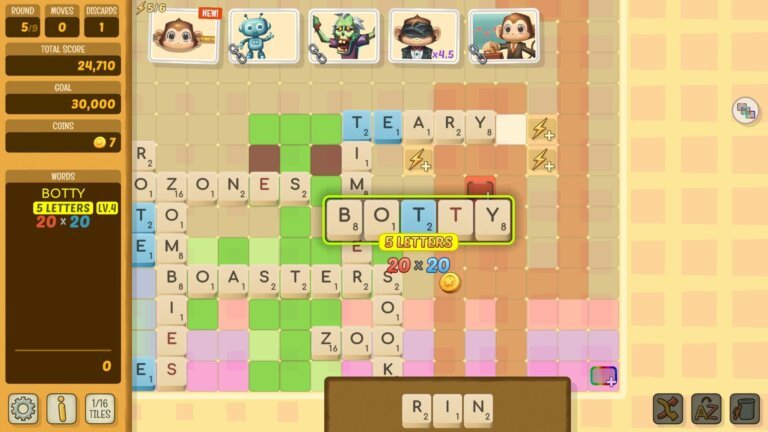
Renowned game developers Steve Ellis and David Doak have created a spelling game called Beyond Words, which features innovative gameplay mechanics that differentiate it from other word game roguelikes. Players navigate a Scrabble-like board aiming for a target score within a limited number of moves, with progressively challenging rounds and a boss round introducing unique gameplay modifiers. Between rounds, players can acquire cards that activate bonuses to enhance scoring potential. The game boasts an expansive dictionary that includes a wide array of terms, adding humor and enjoyment. It includes wildcard tiles for creative word formation and features uniquely shaped maps for each run, enhancing strategic depth. However, the visual presentation has been criticized for lacking a cohesive style. The demo is currently available for free during Steam NextFest.