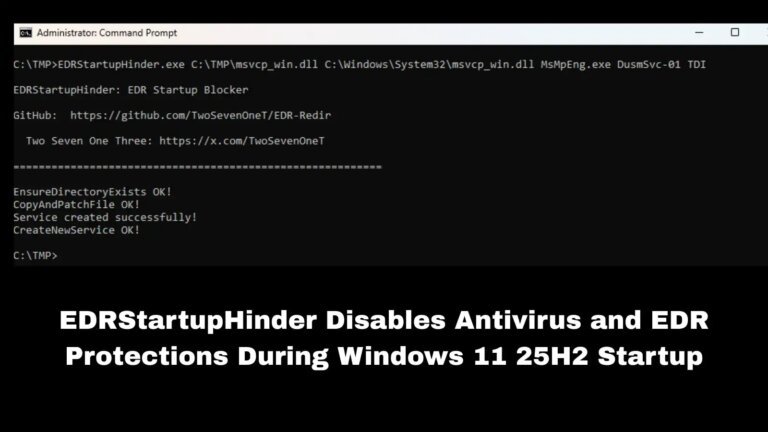
A new tool named EDRStartupHinder was unveiled on January 11, 2026, which allows attackers to inhibit the launch of antivirus and endpoint detection and response (EDR) solutions during the Windows startup process. Developed by security researcher Two Seven One Three, it targets Windows Defender and various commercial security products on Windows 11 25H2 systems by redirecting essential system DLLs during boot using the Windows Bindlink API and Protected Process Light (PPL) security mechanisms.
The tool employs a four-step attack chain that includes creating a malicious service with higher priority than the targeted security services, redirecting critical DLLs to attacker-controlled locations, and modifying a byte in the PE header of the DLLs to cause PPL-protected processes to refuse loading them. This results in the termination of the security software. EDRStartupHinder has been tested successfully against Windows Defender and other unnamed antivirus products, demonstrating its effectiveness in preventing these security solutions from launching.
The source code for EDRStartupHinder is publicly available on GitHub, raising concerns about its potential misuse. Security teams are advised to monitor for Bindlink activity, unauthorized service creation, and registry modifications related to service groups and startup configurations to detect this attack vector. Microsoft has not yet issued any statements regarding patches or mitigations for this technique.