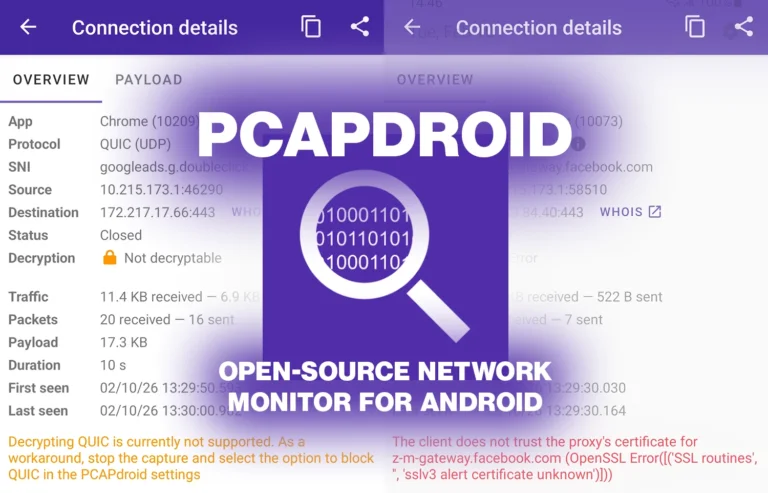
PCAPdroid is a free, open-source application for monitoring network traffic on Android devices. Users can capture traffic by accepting a VPN request and can view active and historical connections, detailing the application, protocol, destination address, and connection status. Traffic can be categorized by application, providing information such as installation date, version, and permissions. PCAPdroid offers various dump modes, allowing users to view traffic in real-time or save it as a PCAP file, and enables sharing captures via a local web page or forwarding live traffic to another machine using UDP or TCP. The app can extract information from captured traffic, including DNS requests, TLS server names, and HTTP requests. It also has the capability to decrypt HTTPS/TLS traffic, which requires a setup process involving a helper add-on and a certificate. Successful decryption allows users to view and export previously encrypted traffic, although not all apps support this feature.