Surfshark is offering a promotion from February 2 to February 23, 2026, allowing users to get antivirus protection for [openai_gpt model="gpt-4o-mini" prompt="Summarize the content and extract only the fact described in the text bellow. The summary shall NOT include a title, introduction and conclusion. Text: Surfshark is currently offering an enticing promotion that allows users to secure antivirus protection for just [cyberseo_openai model="gpt-4o-mini" prompt="Rewrite a news story for a business publication, in a calm style with creativity and flair based on text below, making sure it reads like human-written text in a natural way. The article shall NOT include a title, introduction and conclusion. The article shall NOT start from a title. Response language English. Generate HTML-formatted content using tag for a sub-heading. You can use only , , , , and HTML tags if necessary. Text: Surfshark's limited time February deal means you can grab antivirus for $0.30 per month, alongside one of the best VPNs.Two-year Surfshark One plans, with three extra months free, work out at $2.29 per month ($61.83 upfront pre-tax). This is Surfshark's second tier of plan and sees the inclusion of antivirus, data alerts, and scam protection. The offer is running from February 2-23, 2026, so you'd better act fast.For a full rundown of why we rate Surfshark so highly, you can read our Surfshark VPN review.
VPN plus dedicated antivirus
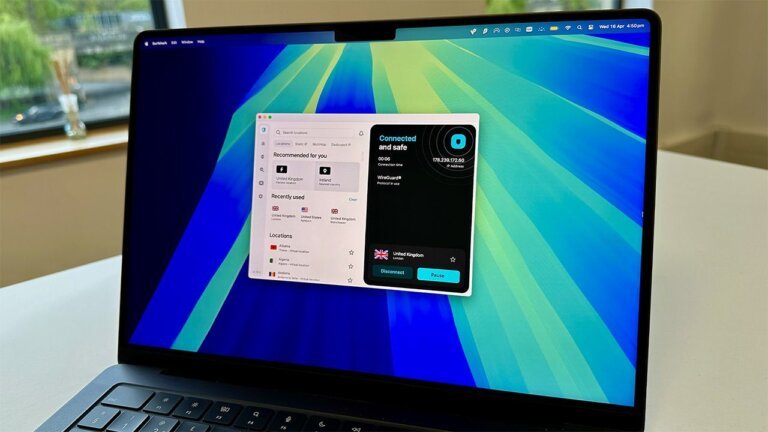
A 27 month Surfshark One plan costs $2.29 per month ($61.83 upfront pre-tax) and comes with a 30-day money-back guarantee.You can protect your data with the best cheap VPN out there. You'll benefit from unlimited device connections, a simple and easy to use VPN, and blistering speeds of up to 1,615 Mbps. There's 4,500+ servers worldwide, covering 142 locations in 100 countries.
(Image credit: Future)
Surfshark is one of the only leading VPNs to offer dedicated antivirus. It's backed by Avira and allows you to run a full device scan or opt for a quick one. Surfshark updates its threat list regularly and any suspicious code is sent to its lab for analysis. You can enable real-time protection, with vulnerable areas of your device being checked.Surfshark Antivirus isn't quite as good as big names like McAfee or Norton 360. However, the best antivirus software will cost you more per month than most VPN plans. So being able to pick up Surfshark Antivirus for an extra $0.30 per month is a great deal.Alongside antivirus, Surfshark One brings an email scam checker and data alerts. Alerts cover personal data, ID, and credit card leaks, plus personal data security reports. You'll also get access to Surfshark's Web Content Blocker and secure search – providing organic search results, free from ads and trackers.
(Image credit: Future)
Surfshark's other plans
Surfshark One is the VPN's best value plan but it has two others. Surfshark Starter is its entry plan and it costs $1.99 per month ($53.73 upfront pre-tax) for 27 months of protection.There's no antivirus, but you'll see fast speeds and powerful streaming unblocking, along with unlimited device connections and class-leading security and privacy. Surfshark has an audited no-logs policy and it is now post-quantum secure. There's also unique features like Alternative ID, which allows you to create a fake alias online.Surfshark One+ is its most expensive plan. You get everything included in previous plans and unlock ID theft protection and the data removal service Incogni.ID theft protection is only available to users in the US (except New York state) and provides up to $1 million of ID theft coverage. Incogni data removal service will send data deletion requests to numerous data brokers, reducing the amount of spam and scam emails you'll receive.Surfshark One+ costs $4.19 per month ($113.13 upfront pre-tax) for 27 months of protection. All Surfshark plans come with a 30-day money-back guarantee.
Today's best Surfshark deals
Disclaimer
We test and review VPN services in the context of legal recreational uses. For example: 1. Accessing a service from another country (subject to the terms and conditions of that service). 2. Protecting your online security and strengthening your online privacy when abroad. We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing." temperature="0.3" top_p="1.0" best_of="1" presence_penalty="0.1" ].30 per month when bundled with one of the industry's leading VPN services. This limited-time offer, available from February 2 to February 23, 2026, features a two-year Surfshark One plan, which includes three additional months free, bringing the total cost down to .29 per month, or .83 upfront before taxes. This plan not only provides a robust VPN service but also incorporates antivirus capabilities, data alerts, and scam protection.
VPN plus dedicated antivirus
The 27-month Surfshark One plan is priced at .29 per month, with a total upfront cost of .83 before taxes, and it comes with a reassuring 30-day money-back guarantee. Users can enjoy unlimited device connections, a user-friendly interface, and impressive speeds of up to 1,615 Mbps, supported by a network of over 4,500 servers across 142 locations in 100 countries.
(Image credit: Future)
What sets Surfshark apart is its inclusion of dedicated antivirus software, powered by Avira. Users can choose between a comprehensive device scan or a quicker option, with the antivirus software regularly updated to combat emerging threats. Any suspicious activity is promptly analyzed in Surfshark's lab, and users can enable real-time protection to safeguard vulnerable areas of their devices. While Surfshark Antivirus may not rival the likes of McAfee or Norton 360, its affordability at an additional [cyberseo_openai model="gpt-4o-mini" prompt="Rewrite a news story for a business publication, in a calm style with creativity and flair based on text below, making sure it reads like human-written text in a natural way. The article shall NOT include a title, introduction and conclusion. The article shall NOT start from a title. Response language English. Generate HTML-formatted content using tag for a sub-heading. You can use only , , , , and HTML tags if necessary. Text: Surfshark's limited time February deal means you can grab antivirus for $0.30 per month, alongside one of the best VPNs.Two-year Surfshark One plans, with three extra months free, work out at $2.29 per month ($61.83 upfront pre-tax). This is Surfshark's second tier of plan and sees the inclusion of antivirus, data alerts, and scam protection. The offer is running from February 2-23, 2026, so you'd better act fast.For a full rundown of why we rate Surfshark so highly, you can read our Surfshark VPN review.
VPN plus dedicated antivirus
A 27 month Surfshark One plan costs $2.29 per month ($61.83 upfront pre-tax) and comes with a 30-day money-back guarantee.You can protect your data with the best cheap VPN out there. You'll benefit from unlimited device connections, a simple and easy to use VPN, and blistering speeds of up to 1,615 Mbps. There's 4,500+ servers worldwide, covering 142 locations in 100 countries.
(Image credit: Future)
Surfshark is one of the only leading VPNs to offer dedicated antivirus. It's backed by Avira and allows you to run a full device scan or opt for a quick one. Surfshark updates its threat list regularly and any suspicious code is sent to its lab for analysis. You can enable real-time protection, with vulnerable areas of your device being checked.Surfshark Antivirus isn't quite as good as big names like McAfee or Norton 360. However, the best antivirus software will cost you more per month than most VPN plans. So being able to pick up Surfshark Antivirus for an extra $0.30 per month is a great deal.Alongside antivirus, Surfshark One brings an email scam checker and data alerts. Alerts cover personal data, ID, and credit card leaks, plus personal data security reports. You'll also get access to Surfshark's Web Content Blocker and secure search – providing organic search results, free from ads and trackers.
(Image credit: Future)
Surfshark's other plans
Surfshark One is the VPN's best value plan but it has two others. Surfshark Starter is its entry plan and it costs $1.99 per month ($53.73 upfront pre-tax) for 27 months of protection.There's no antivirus, but you'll see fast speeds and powerful streaming unblocking, along with unlimited device connections and class-leading security and privacy. Surfshark has an audited no-logs policy and it is now post-quantum secure. There's also unique features like Alternative ID, which allows you to create a fake alias online.Surfshark One+ is its most expensive plan. You get everything included in previous plans and unlock ID theft protection and the data removal service Incogni.ID theft protection is only available to users in the US (except New York state) and provides up to $1 million of ID theft coverage. Incogni data removal service will send data deletion requests to numerous data brokers, reducing the amount of spam and scam emails you'll receive.Surfshark One+ costs $4.19 per month ($113.13 upfront pre-tax) for 27 months of protection. All Surfshark plans come with a 30-day money-back guarantee.
Today's best Surfshark deals
Disclaimer
We test and review VPN services in the context of legal recreational uses. For example: 1. Accessing a service from another country (subject to the terms and conditions of that service). 2. Protecting your online security and strengthening your online privacy when abroad. We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing." temperature="0.3" top_p="1.0" best_of="1" presence_penalty="0.1" ].30 per month makes it an attractive option for those seeking comprehensive online security.
In addition to antivirus protection, Surfshark One offers an email scam checker and data alerts that monitor personal data, including ID and credit card leaks, along with personalized data security reports. Users also gain access to Surfshark's Web Content Blocker and secure search features, ensuring a cleaner and more private browsing experience.
(Image credit: Future)
Surfshark's other plans
While Surfshark One is positioned as the best value offering, the company also provides two additional plans. The Surfshark Starter plan, priced at .99 per month (.73 upfront pre-tax) for 27 months, does not include antivirus but still delivers fast speeds, powerful streaming capabilities, unlimited device connections, and top-tier security and privacy features. Surfshark adheres to a strict no-logs policy and is now post-quantum secure, with unique offerings like Alternative ID, which allows users to create a pseudonym for online activities.
For those seeking more comprehensive coverage, Surfshark One+ is the premium plan that encompasses all features from previous tiers while adding ID theft protection and the data removal service, Incogni. This ID theft protection service, available to users in the U.S. (excluding New York state), offers coverage of up to million. The Incogni service actively requests data deletion from various data brokers, helping to minimize unwanted spam and scam emails. Surfshark One+ is available for .19 per month (3.13 upfront pre-tax) for 27 months, and all plans come with a 30-day money-back guarantee.
Today's best Surfshark deals" max_tokens="3500" temperature="0.3" top_p="1.0" best_of="1" presence_penalty="0.1" frequency_penalty="frequency_penalty"].30 per month when bundled with its VPN service. The two-year Surfshark One plan costs .29 per month (.83 upfront pre-tax) and includes three additional months free. This plan features antivirus, data alerts, and scam protection, along with unlimited device connections and speeds of up to 1,615 Mbps across over 4,500 servers in 100 countries.
Surfshark's antivirus, powered by Avira, allows for full or quick device scans and offers real-time protection. While it may not be as robust as competitors like McAfee or Norton 360, it provides a cost-effective option for users. Additionally, Surfshark One includes an email scam checker and alerts for personal data leaks.
Surfshark also has two other plans: the Surfshark Starter plan at .99 per month (.73 upfront pre-tax) for 27 months, which does not include antivirus, and the Surfshark One+ plan at .19 per month (3.13 upfront pre-tax) for 27 months, which adds ID theft protection and the Incogni data removal service. All plans come with a 30-day money-back guarantee.