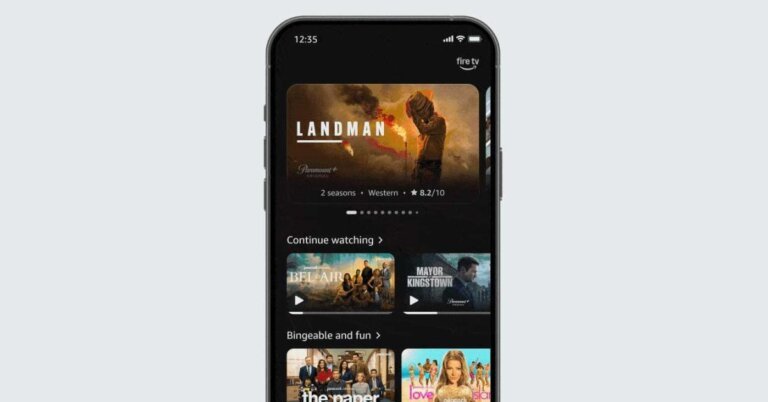
Amazon has updated its Fire TV Android app with a new user interface (UI) that focuses on simplicity and intuitive navigation. The redesign features a cleaner layout, improved menus, and clearer typography to enhance user-friendliness. Users can now browse movie and series recommendations, read summaries, and create a personal watchlist directly from the app's homepage. The app also functions as a remote control for compatible televisions linked to the same Amazon account, allowing users to navigate menus and control playback without a physical remote. This updated interface aligns with a broader refresh of Fire TV software and is being rolled out in several countries, including the US, Brazil, Canada, France, Germany, India, Italy, Japan, Mexico, Spain, and the UK.