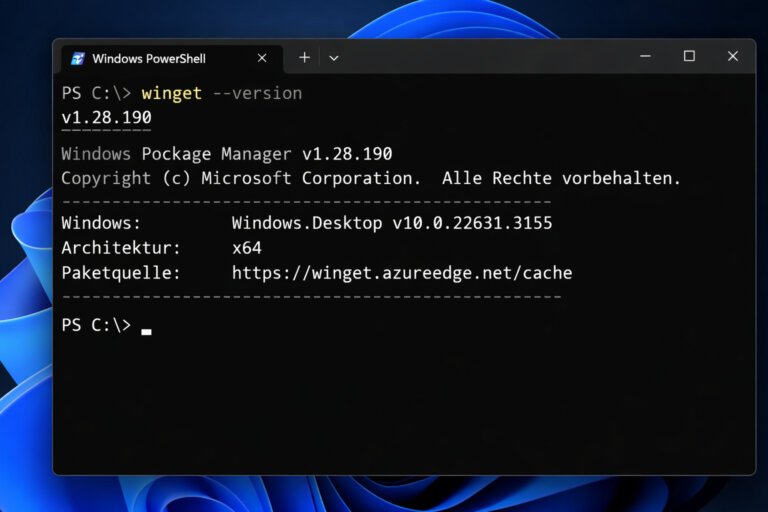
Microsoft has launched WinGet 1.28.190, aligning its version number with App Installer to resolve discrepancies. The previous version 1.12.470 has been replaced by this update. Key changes include consistent directory separators for portable packages, compatibility of the –suppress-initial-details option with winget configure test, corrections to the experimental “font” property, and the introduction of the experimental sourceEdit feature, which allows users to set a source for package management. The update signifies a consolidation of versioning and enhances clarity for users and administrators.