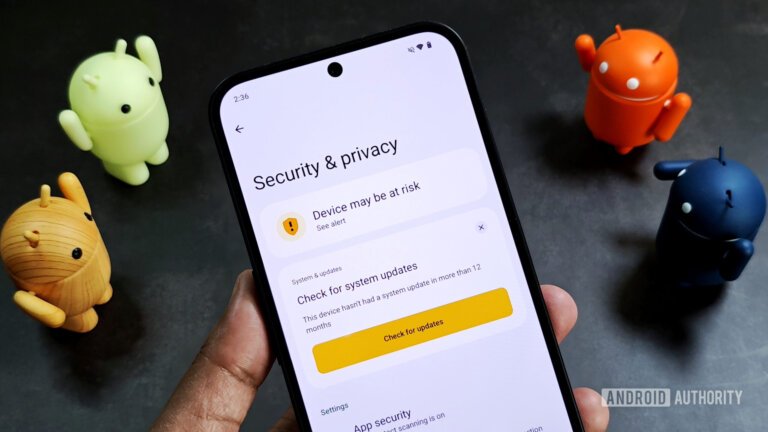
Google has reported significant improvements in app security for Android in 2025, preventing over 1.75 million policy-violating apps from entering the Play Store and removing more than 80,000 developer accounts attempting to distribute malware. The integration of AI models into the app review process has enhanced the speed and accuracy of identifying malicious patterns. Additionally, Google blocked over 255,000 apps from requesting unnecessary sensitive data and eliminated 160 million spam ratings and reviews. Google Play Protect now evaluates over 350 billion apps daily, identifying 27 million new malicious apps outside the Play Store and blocking 266 million risky installation attempts across 185 markets. A new measure has been implemented to prevent users from disabling Play Protect during phone calls to combat social engineering tactics. Future plans include democratizing developer verification and simplifying protection against "tapjacking" attacks in Android 16.