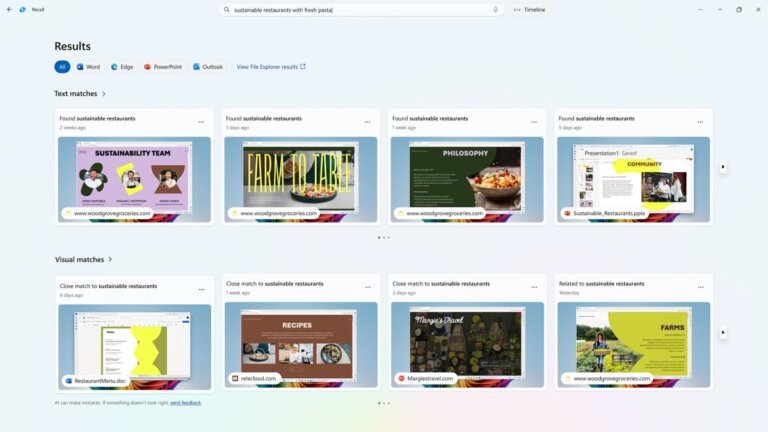
Microsoft's latest Windows 25H2 builds have introduced AI features, but users cannot easily disable them through the interface, leading many to use third-party tools like the RemoveWindowsAI PowerShell script to eliminate components such as Copilot, Recall, and Input Insights. Windows Recall captures screenshots for AI-driven searches, raising privacy concerns due to the creation of a local database of full screenshots. Microsoft has also disabled phone activation for Windows 11, requiring internet connectivity for activation. The RemoveWindowsAI tool removes appx packages associated with AI, ensuring they cannot be reinstalled. Microsoft has announced the discontinuation of support for Windows 11 SE by October 13, 2026, impacting schools that rely on this version. Virtualization, such as using Proxmox, is recommended for users wary of telemetry practices. The RemoveWindowsAI project is evolving to enhance its capabilities in response to Microsoft's AI feature additions. Enterprise deployments are advised to test removal strategies in controlled environments, though some antivirus programs may flag the tool as malicious. Privacy advocates are concerned about the implications of Microsoft's changes on user control and data collection.