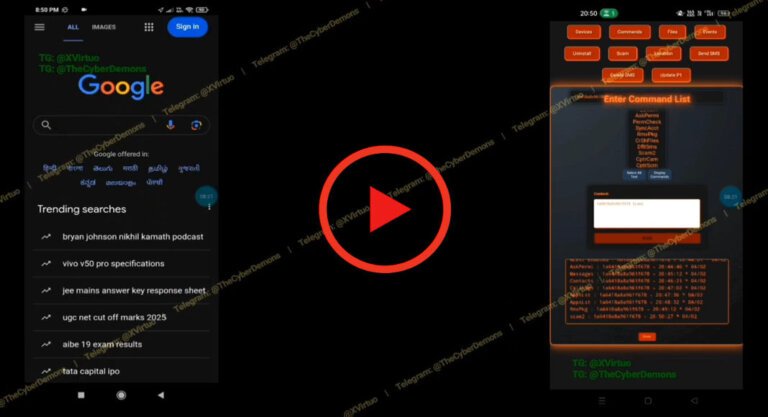
A new Android malware named Albiriox has emerged, marketed as malware-as-a-service (MaaS). It features a hard-coded list of over 400 applications, including banking and cryptocurrency platforms, and is distributed through social engineering tactics using dropper applications. Initially advertised in late September 2025, it became a full MaaS offering by October, with Russian-speaking threat actors behind its development. Albiriox allows remote control of compromised devices via an unencrypted TCP socket connection and Virtual Network Computing (VNC), enabling attackers to extract sensitive information and perform overlay attacks for credential theft. One campaign targeted victims in Austria using German-language lures and counterfeit Google Play Store listings. Albiriox also utilizes Android's accessibility services to bypass security measures and employs a novel distribution strategy involving a counterfeit website that collects phone numbers. Additionally, another Android MaaS tool, RadzaRat, was introduced, masquerading as a file management utility while offering extensive surveillance and remote control capabilities. RadzaRat can log keystrokes and maintain persistence through specific permissions, highlighting a trend in the availability of sophisticated cybercrime tools.