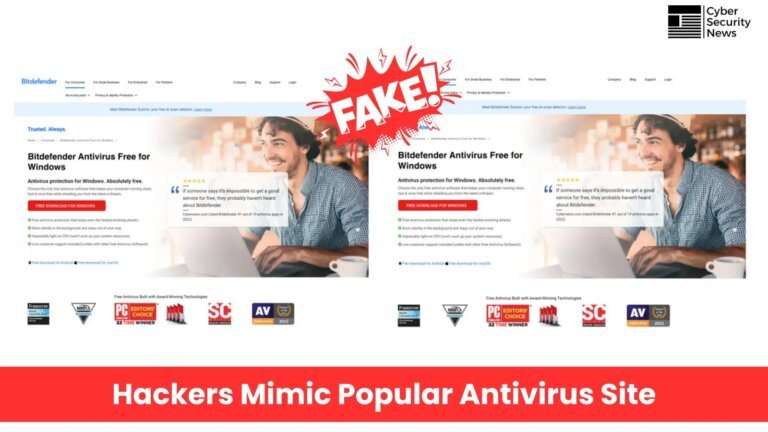
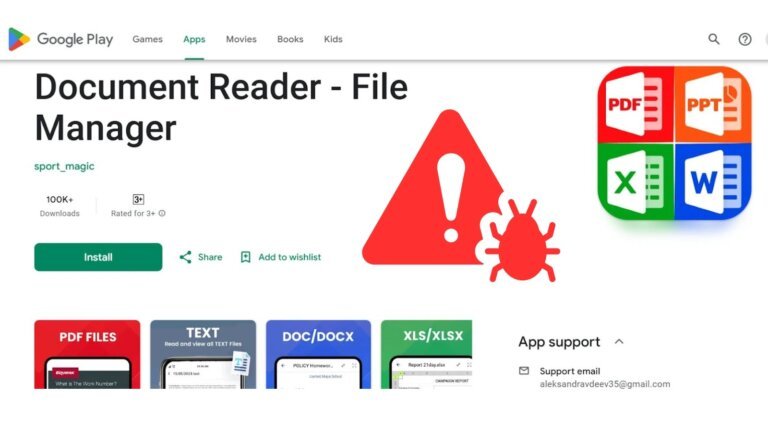
Cybersecurity experts have highlighted the risks of typosquatting, where developers accidentally download malicious packages due to typographical errors. A report from Checkmarx reveals that attackers exploit this trust by creating counterfeit packages that can grant unauthorized access to systems. Malicious packages have been found in the Python Package Index (PyPI) and can enable remote control, posing serious threats to system integrity. Attackers employ a cross-platform strategy, mixing names from different programming environments to target unsuspecting users. On Windows, malware can create scheduled tasks and disable antivirus protections, while on Linux, certain packages facilitate encrypted reverse shells for data exfiltration. Although the malicious packages have been removed, the threat remains, prompting developers to verify package sources and spellings. Checkmarx recommends organizations conduct audits of deployed packages and scrutinize application code to enhance security.