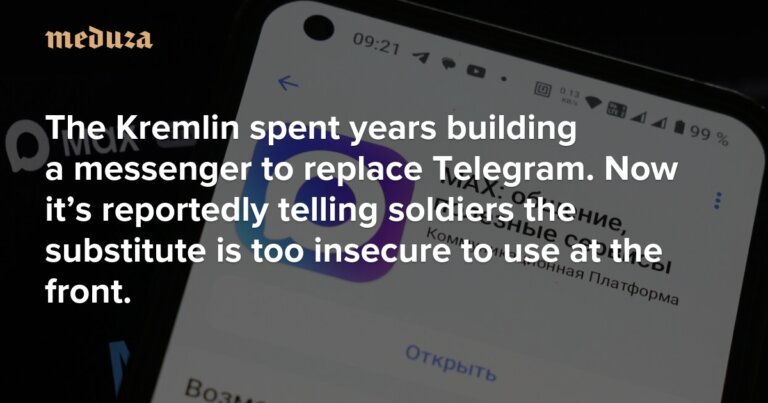
Russian military personnel have been advised to stop using the messaging application Max due to security concerns, as reported by Mediazona. This recommendation follows intensified restrictions on Telegram, which began in the summer of 2025. The Federal Security Service (FSB) has warned that Ukrainian forces can intercept Telegram communications, prompting worries about the safety of sensitive information. Access to Telegram has been increasingly limited, with plans for further restrictions on media file access reported by RBC. Pro-war advocates, including Sergey Mironov, have criticized these limitations and defended Telegram as a reliable communication tool. Despite the Kremlin's claims that troops do not rely on Telegram, the Russian Defense Ministry asserts that they use standard communications equipment and a domestically developed messenger. On February 18, Russian Digital Development Minister Maksut Shadaev stated that Telegram would not be blocked for frontline use for now.