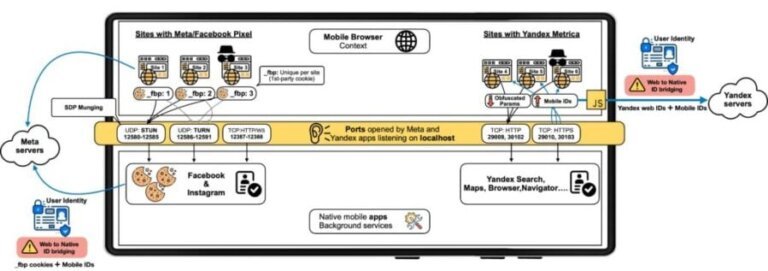
Recent findings from IMDEA Networks Institute indicate that Facebook and Instagram apps have been tracking Android users' web browsing activities without consent, bypassing privacy controls and functioning even in incognito mode. This tracking affects millions of websites using Meta's tracking code. Yandex has employed similar tracking techniques since 2017, creating a cross-platform surveillance network. The tracking exploits Android’s permission system by establishing background services that listen on network ports, allowing the apps to capture browsing data and associate it with users' accounts. Meta's pixel is present on about 5.8 million websites, while Yandex Metrica is on around 3 million sites, potentially impacting billions of users. Approximately 78% of sites with Meta’s pixel and 84% of Yandex's sites attempted localhost communications without user consent. This tracking method operates at the operating system level, unaffected by cookie clearing, incognito modes, or privacy settings. Researchers have demonstrated that malicious apps could exploit this technique to gather users' browsing histories. Many website operators were unaware of these localhost communications, leading to confusion and complaints. In response, major browser vendors are implementing measures to block these tracking methods. Meta ceased this tracking on June 3rd, coinciding with the research's public release. The research highlights a significant security gap in mobile platforms regarding localhost communications, emphasizing the need for stricter policies and vetting processes.