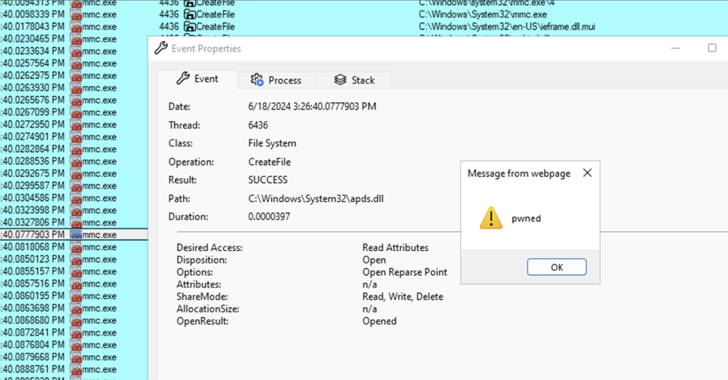
A newly identified threat actor, EncryptHub, is involved in Windows zero-day attacks exploiting a vulnerability in the Microsoft Management Console (MMC), known as 'MSC EvilTwin' (CVE-2025-26633). This vulnerability allows attackers to bypass Windows file reputation protections by manipulating MSC files on unpatched systems. Attackers can execute code without user alerts through email or web-based attacks. Trend Micro's research indicates that EncryptHub has used CVE-2025-26633 to deploy various malicious payloads, including the EncryptHub stealer and DarkWisp backdoor, to extract data from compromised systems. The threat actor employs multiple delivery methods and custom payloads to maintain persistence and exfiltrate sensitive information. EncryptHub has been linked to breaches affecting at least 618 organizations globally and is known to deploy ransomware after stealing sensitive data. Microsoft has also patched another zero-day vulnerability (CVE-2025-24983) in the Windows Win32 Kernel Subsystem.