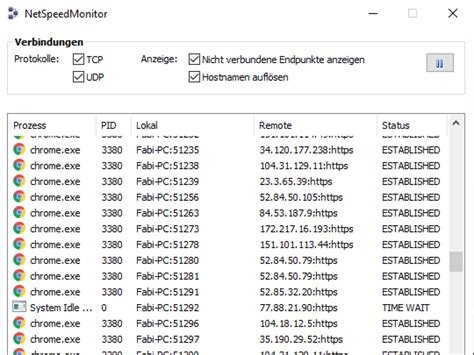
NetSpeedMonitor is a free tool for Windows 10 64-bit that displays real-time upload and download speeds in the taskbar. It features real-time monitoring, taskbar integration, a customizable interface, low resource usage, and some historical data insights. It helps troubleshoot network issues, monitor data usage, and identify bandwidth-hogging applications. To download, users should search for compatible versions online, check user reviews, and download from trusted sources. Installation involves extracting files, running the installer, and selecting the appropriate network adapter. Configuration options include customizing display units, update intervals, and font colors. Alternatives to NetSpeedMonitor include DU Meter, NetWorx, GlassWire, and Windows Resource Monitor.