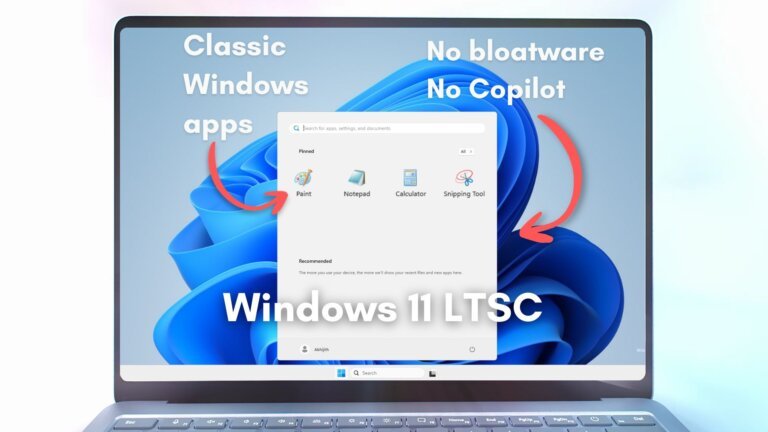
- Developers on Google Play can now use their own billing systems alongside Google Play's payment system
- The service fee for in-app purchases tied to new installs will be 20%, but developers in certain programs will pay 15%
- Developers using Google Play's billing system will pay a separate 5% billing fee in certain regions
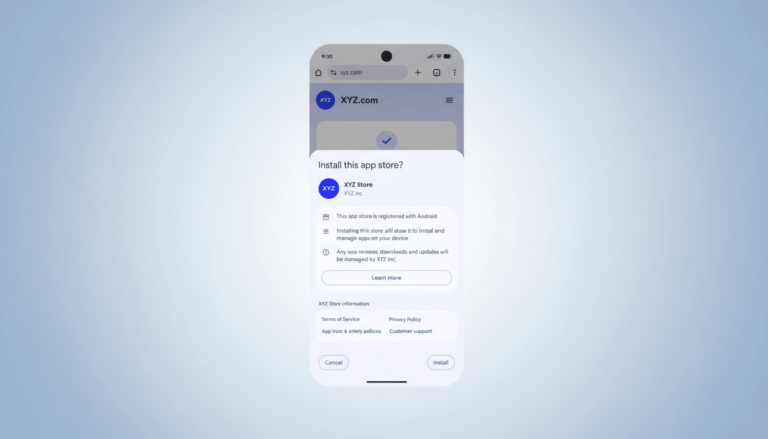
- Google is launching a Registered App Stores program to simplify the installation of third-party Android stores