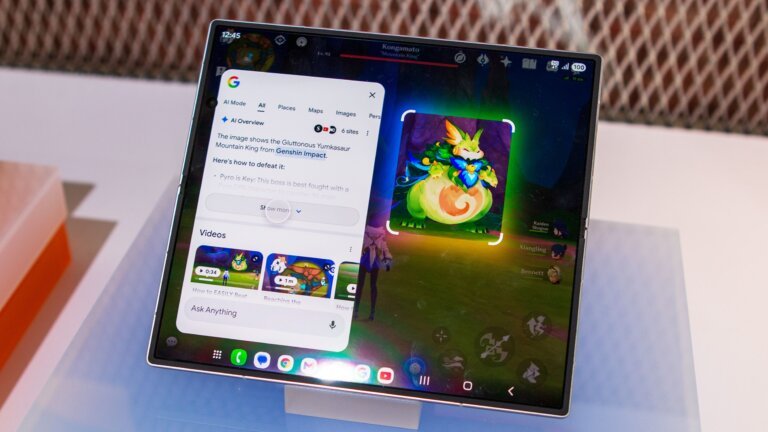
Circle to Search has reached its second anniversary, marking a significant milestone for Google. It was introduced to Android as a practical application of artificial intelligence and has evolved to include enhanced functionalities relevant in 2026. Users can access the generative AI model Nano Banana directly through Circle to Search for image creation and editing, streamlining the remixing process. The tool also features a full-screen translation capability that allows instant translation of text displayed on screens across various apps and websites, supporting multiple languages and enabling scrolling translations. Additionally, Circle to Search can scan QR codes and barcodes displayed on screens, functioning similarly to the Camera app. Its capabilities include text selection, image searching, generative AI, code scanning, song recognition, and on-screen translation, making it a versatile tool that enhances user experience. The Google Pixel 10 is highlighted as an ideal companion for Circle to Search, equipped with AI-powered tools that enhance overall user experience.