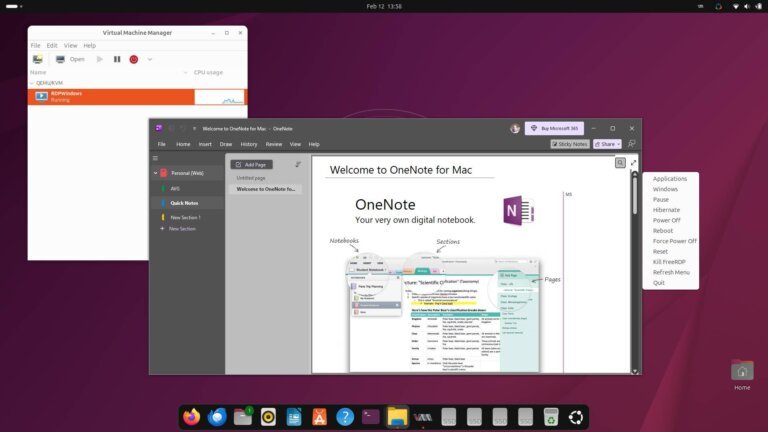
WinApps and WinBoat are two solutions for running Windows applications on Linux. WinApps, developed since 2020 by Ben Curtis, allows users to run a genuine copy of Windows in a virtual machine (VM) and export individual applications to the Linux desktop using Microsoft's Remote Desktop Protocol (RDP). It supports various methods, including Docker, Podman, and KVM virtualization, with KVM offering extensive customization but requiring a more complex setup. WinBoat, a newer application at version 0.9.0, simplifies the user experience by automating much of the setup process and requires only Docker and FreeRDP to be installed. WinBoat is designed for ease of use, making it accessible for users less comfortable with technical configurations. Both tools allow users to run Windows software that may not work well under WINE, but running a full Windows OS in a VM involves licensing, maintenance, and resource considerations.