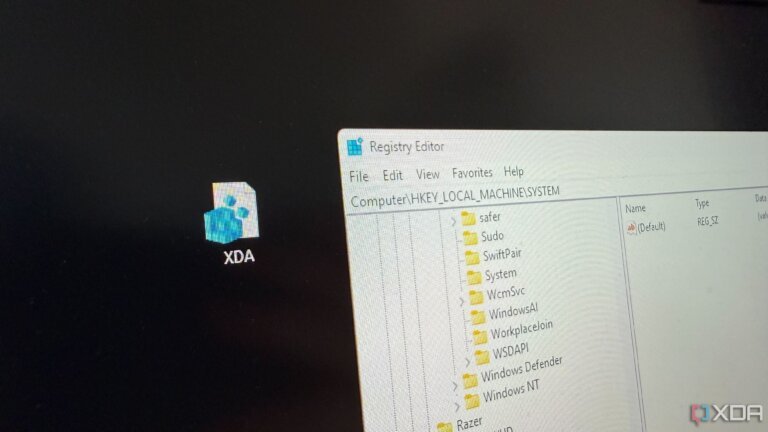
Windows 11 has integrated AI features, including Copilot, which is pinned to the taskbar and embedded in applications like Notepad and Paint. Users cannot universally disable these features, although individual toggles exist. A community script called RemoveWindowsAI has been created to disable Windows AI features at the system level and modify Windows Update settings to prevent reinstallation. The script targets Copilot, Recall, and their integrations, allowing users to disable all features or select specific components. It operates by making registry changes and aims to eliminate visible AI entry points while maintaining their disabled status across updates. When executed, RemoveWindowsAI removes Copilot from the taskbar, uninstalls the app, and disables AI functionalities in applications. Users run the script through Windows PowerShell 5.1, and it can be rerun to re-enable features. The tool provides a consistent experience but has limitations, as it may not address new AI features or changes from major Windows updates.