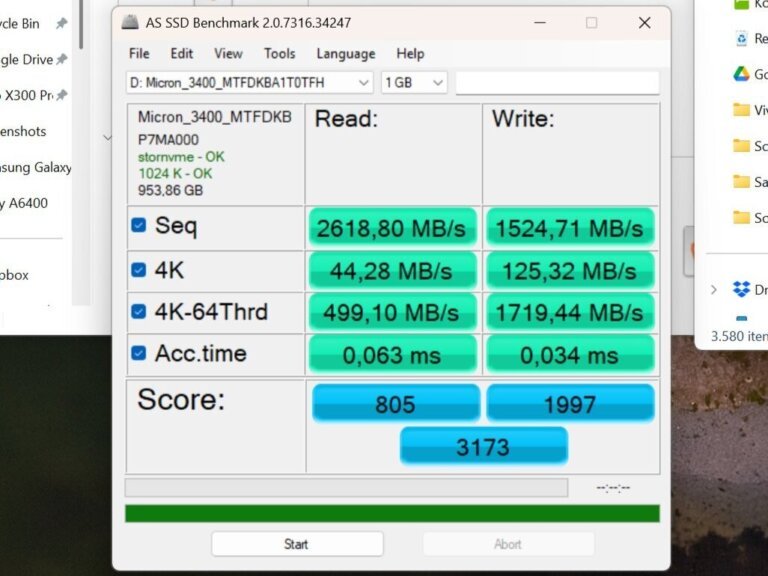
Recent discoveries have revealed a registry tweak that can enhance the performance of NVMe SSDs on Windows 11, particularly improving random 4K speeds. Traditionally, Windows has treated most drives as SCSI, limiting the potential of NVMe drives. Microsoft is introducing native NVMe support in Windows Server 2025, which bypasses the SCSI conversion process for improved speed and efficiency. Users can achieve similar enhancements on Windows 11 through specific registry modifications, which must be done at their own risk. The necessary driver is included in recent updates for both Windows Server 2025 and Windows 11. Users need to adjust three registry values to enable this functionality. Once modified, NVMe drives will appear under 'Storage Media' in Device Manager. Reports indicate significant performance gains, with one user noting increases of 45% in random 4K read and 49% in write performance. Microsoft suggests enterprise users could see up to 80% higher IOPS and a 45% reduction in CPU cycles. The WD Black SN8100 SSD is noted for its high random 4K speeds, loading games faster than competitors. Many users have pointed out that Linux has had native NVMe support for some time.