Jen Easterly has been appointed as the new Chief Executive Officer of the RSA Conference. She is a cybersecurity expert and former Director of the Cybersecurity and Infrastructure Security Agency (CISA).
Palo Alto Networks has released security updates for a vulnerability (CVE-2026-0227) with a CVSS score of 7.7 affecting its GlobalProtect Gateway and Portal, which can cause a denial-of-service condition in PAN-OS software.
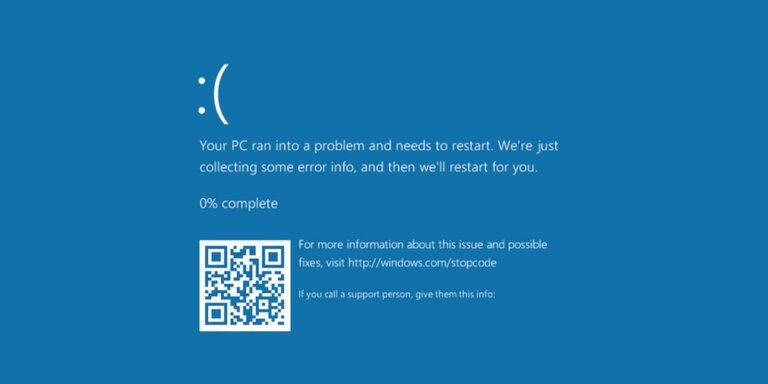
The January 2026 security update from Microsoft has caused connection and authentication failures in Azure Virtual Desktop and Windows 365, affecting users across various Windows versions. Microsoft is working on a resolution.
The chief constable of West Midlands Police acknowledged an error by Microsoft’s Copilot AI in generating a fictional intelligence report. Microsoft has not confirmed Copilot's involvement.
Britain’s National Cyber Security Centre (NCSC) has collaborated with Five Eyes partners to provide guidance on securing industrial operational technology, highlighting risks associated with remotely monitored systems.
Kyowon, a South Korean conglomerate, confirmed a ransomware attack on January 10 that may have compromised customer information, affecting approximately 5.5 million members.
Researchers at Varonis have identified a new attack technique called "Reprompt" that allows data exfiltration from Microsoft Copilot via a malicious link, exploiting a Parameter 2 Prompt (P2P) injection technique.
Central Maine Healthcare is notifying over 145,000 patients about a data breach that compromised personal, treatment, and health insurance information, discovered on June 1.