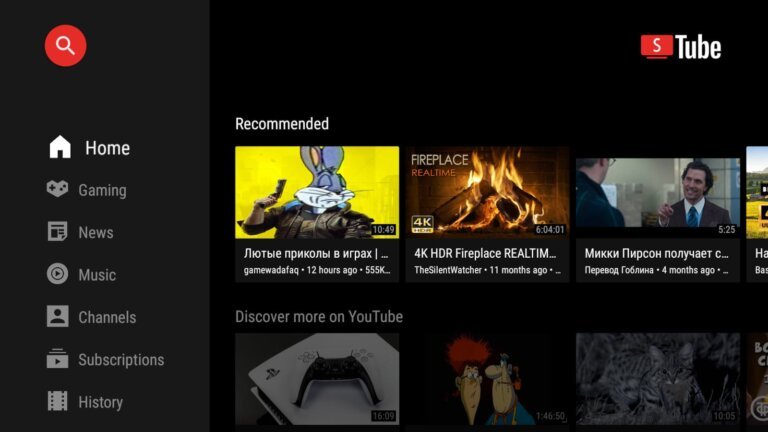
An attacker gained access to the developer's signing keys for SmartTube, an open-source YouTube client for Android TV, leading to a malicious update being distributed. The developer, Yuriy Yuliskov, confirmed the compromise and plans to release a new version with a different app ID. Users reported that Play Protect flagged SmartTube as a potential threat. A reverse-engineered version, identified as 30.51, contained a hidden library named libalphasdk.so, which was not part of the public source code and collected device fingerprints without user knowledge. There is currently no evidence linking the malware to account theft or DDoS attacks, but concerns remain. Yuliskov has announced safe beta and stable test builds on Telegram, but they are not yet on GitHub. Users are advised to stay on older verified builds, avoid logging in with premium accounts, and disable auto-updates. Version 30.19 does not trigger Play Protect warnings, suggesting it may be safer.