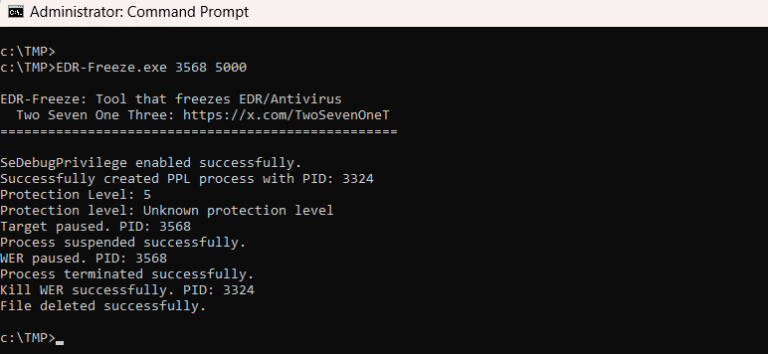
Endpoint detection and response (EDR) systems and antivirus protections are increasingly targeted by threat actors using sophisticated techniques. A new method called EDR-Freeze has been introduced, which utilizes Windows Error Reporting and the MiniDumpWriteDump function to hibernate antivirus processes without needing to install vulnerable drivers. This technique operates entirely in user mode and was disclosed by an anonymous researcher known as Two One Seven Three on Zero Salarium.
The MiniDumpWriteDump function can suspend all threads within a target process during the dump process, which is crucial to avoid memory corruption. The researcher faced challenges with the rapid execution of MiniDumpWriteDump and the security measures protecting EDR and antivirus processes. By reverse-engineering the WerFaultSecure program, the researcher enabled MiniDumpWriteDump for any chosen process and integrated it with the CreateProcessAsPPL tool to bypass Protected Process Light (PPL) protections.
The researcher proposed a race condition attack consisting of four steps: executing WerFaultSecure with WinTCB-level protection, configuring it to dump the target process, monitoring the target process until it is suspended, and then suspending the WerFaultSecure process. A tool to execute this exploit is available on GitHub, and another researcher has developed a KQL rule for its detection. The EDR-Freeze technique exploits a vulnerability in the WerFaultSecure program, addressing the weaknesses of the BYOVD method and allowing flexible control over EDR and antivirus programs.