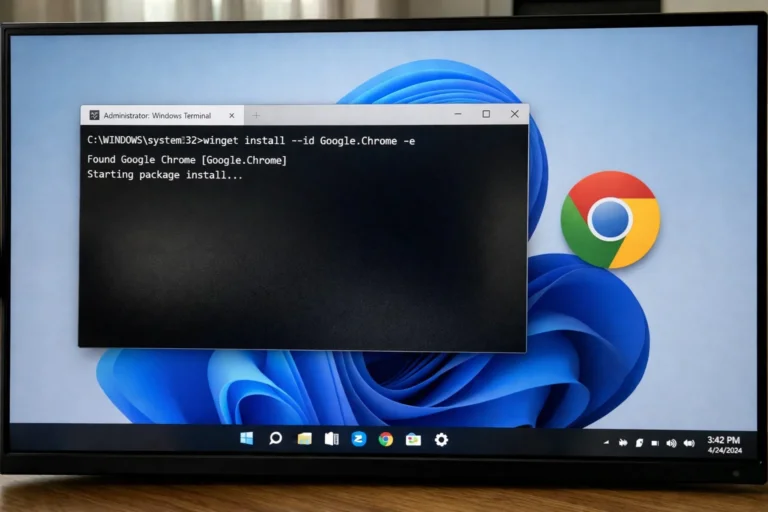
Google Chrome can experience performance issues on Windows due to corrupted profiles, extension conflicts, broken updates, and crashes. A complete uninstall and reinstall often resolves these issues, and the Windows Package Manager (Winget) provides a command-line method for this process.
To uninstall Chrome using Winget, open Terminal as an administrator and run the command PLACEHOLDER7836d906c03bd8f1. After uninstallation, verify it with PLACEHOLDER30cf24d62406b8ee, then reinstall using PLACEHOLDER76e40aae6965d719. For a clean reinstall, delete the leftover user data folder at PLACEHOLDER142352b706501488.
Commands:
- Check installed version:
winget list Google.Chrome
- Uninstall Chrome: winget uninstall Google.Chrome
- Verify removal: winget list Google.Chrome
- Reinstall Chrome: winget install Google.Chrome
- Silent install: winget install Google.Chrome --silent
- Delete leftover data: rmdir /s /q "%LocalAppData%GoogleChrome"
Before executing commands, ensure Winget is available and updated, and that you have administrator privileges. Backup data by enabling Chrome Sync. Close Chrome completely before uninstalling to avoid process interference.
A clean reinstall involves deleting the Chrome user data folder, which removes bookmarks, passwords, and other stored data. Winget is faster and more suitable for scripting and remote management compared to traditional uninstall methods through the Settings app or Control Panel.
Common troubleshooting for Winget includes handling errors related to package recognition, installation blocks, and access issues. If uninstalling fails, terminate any running Chrome processes and retry the command. If unsuccessful, use the Settings app for removal and then Winget for reinstallation.