New York Attorney General Letitia James has filed a lawsuit against Valve, the creator of Steam, regarding loot boxes in games like Counter-Strike 2, Dota 2, and Team Fortress 2, claiming they promote gambling behaviors among youth. The state seeks to stop Valve's use of loot boxes and impose financial penalties. The lawsuit argues that loot boxes resemble traditional slot machines and that items obtained can be traded for real-world value, with a virtual gun skin from Counter-Strike 2 reportedly selling for over a million dollars in 2024. The lawsuit claims Valve intentionally makes high-value items rare to increase their perceived worth and highlights the potential for addiction and illegal gambling, particularly among young people. Valve has not yet responded to the lawsuit.
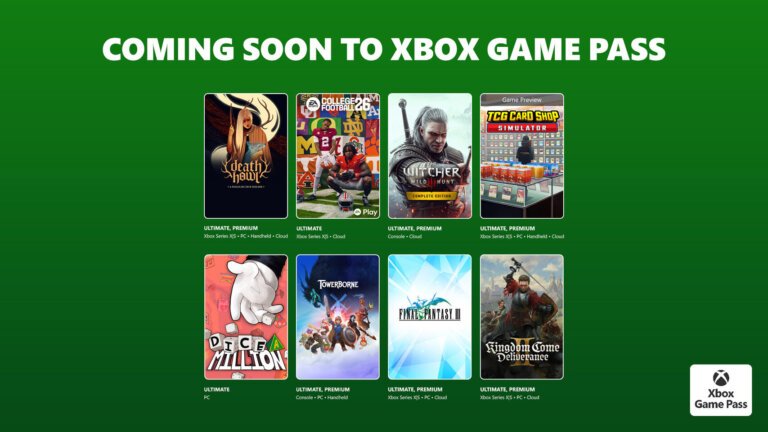
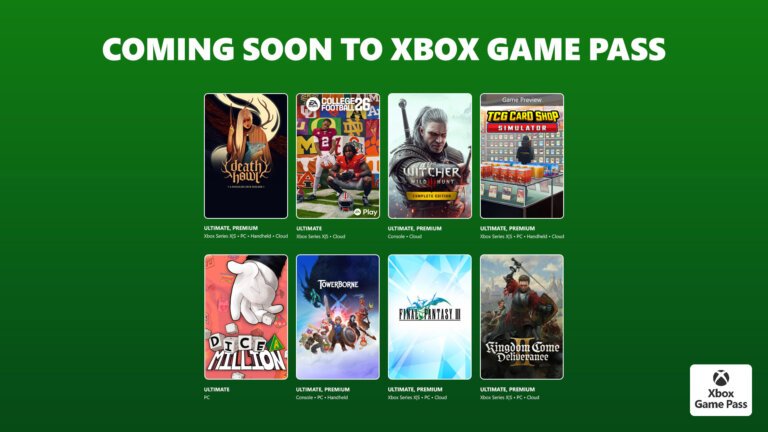
AerialKnight’s DropShot is available on February 17 for Cloud, Xbox Series X|S, Handheld, and PC via Game Pass Ultimate and PC Game Pass. Avatar: Frontiers of Pandora is also available on February 17 for the same platforms, featuring a first-person action-adventure experience. Avowed receives an update on February 17, introducing new playable races, a New Game Plus Mode, and a Photo Mode. Death Howl will launch on February 19 for Cloud, Xbox Series X|S, Handheld, and PC on Game Pass Ultimate and Premium. EA Sports College Football 26 is available on February 19 for Cloud and Xbox Series X|S, allowing players to represent 136 FBS schools. The Witcher 3: Wild Hunt – Complete Edition launches on February 19 for Cloud and Console. TCG Card Shop Simulator enters Game Preview on February 24 for multiple platforms. Dice A Million will be available on PC on February 25 with Xbox Game Pass. Towerborne releases as a complete game on February 26 for Console, Handheld, and PC. Final Fantasy III and Kingdom Come: Deliverance II are set for March 3 on multiple platforms. Menace entered Game Preview on February 5 for PC, and Diablo II: Resurrected was released on February 11 for Console and PC. Overwatch: Season 1: Conquest began on February 10, introducing new heroes. Microsoft Mahjong will feature in-game benefits on February 24 for PC. Titles leaving Game Pass on February 28 include Monster Train, Expeditions: A MudRunner Game, Injustice 2, and Middle Earth: Shadow of War.