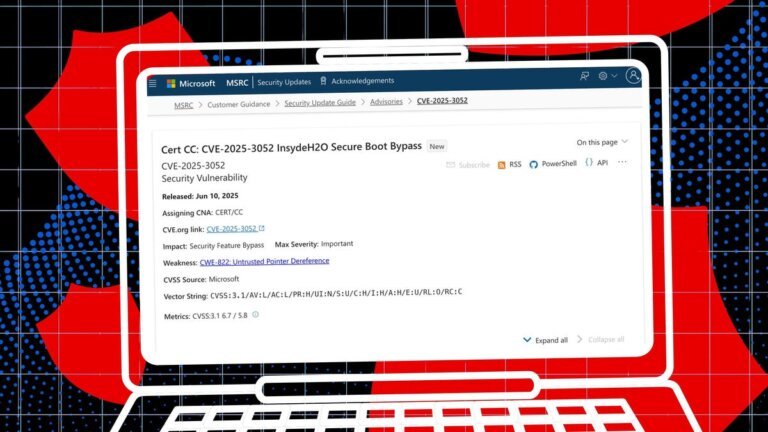
Microsoft updated the Windows Hello face unlock functionality in April, which now fails to operate in low-light environments due to a strategic decision aimed at addressing a spoofing vulnerability. Users of Surface Laptops have reported frustrations as they can no longer access their devices using facial recognition in dark rooms. The update requires color cameras to see a visible face when signing in. Researchers from Nanyang Technological University identified a vulnerability in the system that allowed unauthorized access, although Microsoft categorized it as "important" and stated the likelihood of exploitation remains low. A temporary workaround for users is to disable the webcam through Windows 11's Device Manager, but this renders the camera unusable for other applications.