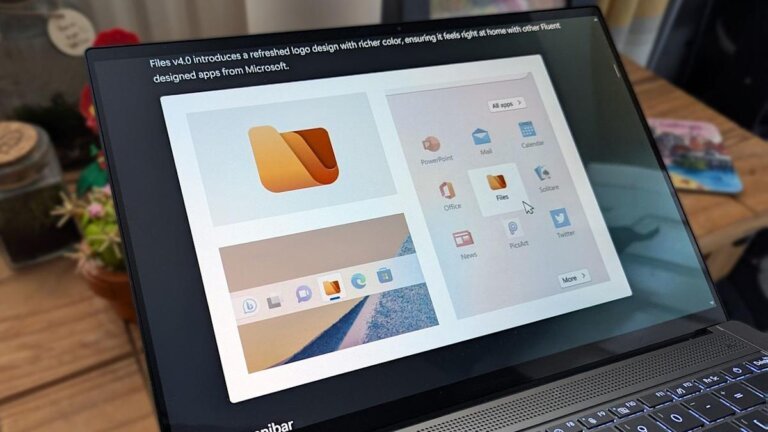
The Files app has been updated to version 4.0.28, featuring an improved right-click context menu, bug fixes, support for the Microsoft Store version of Dropbox, icon customization for URL and shortcut files, and an option to disable smooth scrolling. The update resolves several issues, including problems with the 'Open With' menu, tab switching, and tag searches. The development team is focused on performance improvements, particularly for thumbnail loading times. Microsoft has plans to enhance Windows 11 and address user pain points related to File Explorer.