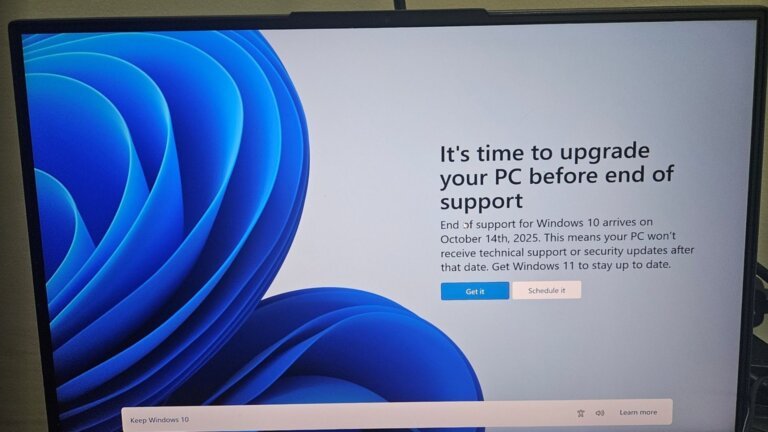
Gartner predicts that the sub-0 entry-level PC segment will disappear by 2028 due to a 130% increase in memory and SSD costs, contributing to a 17% rise in PC prices by 2025. This situation is expected to result in a 10.4% decline in PC shipments this year, the first contraction in over a decade. Consumers are anticipated to keep their devices longer, with business users holding onto PCs for 15% longer and consumers for 20% longer by the end of 2026. The report indicates that elevated RAM and SSD prices will persist longer than expected, influenced by broader inflation trends. Additionally, the anticipated 50% market penetration of AI PCs is now expected to be delayed until 2028.