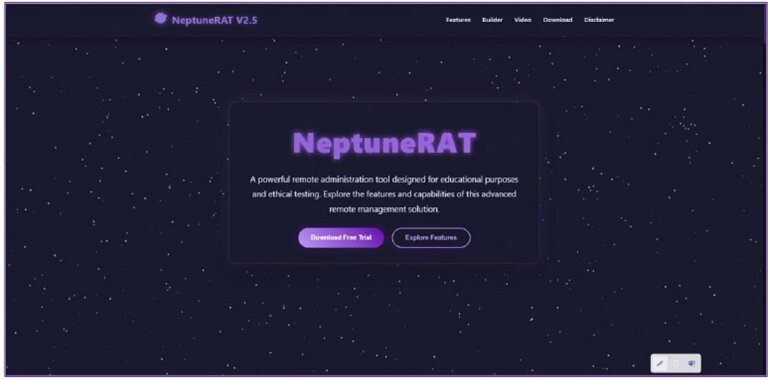
Cybercriminals have released a new malware strain called Neptune RAT, which targets Windows PCs and is capable of stealing cryptocurrencies and passwords, as well as holding data for ransom. It features a crypto clipper that can alter cryptocurrency wallet addresses, a password-stealing function affecting over 270 applications, and ransomware capabilities that lock files until a ransom is paid. The malware can disable antivirus software, monitor victims' screens in real-time, and has the ability to wipe a PC. It is distributed through platforms like GitHub, Telegram, and YouTube, making it difficult for cybersecurity researchers to analyze. Users are advised to be cautious with downloads, consider identity theft protection services, and practice safe browsing habits to mitigate risks.