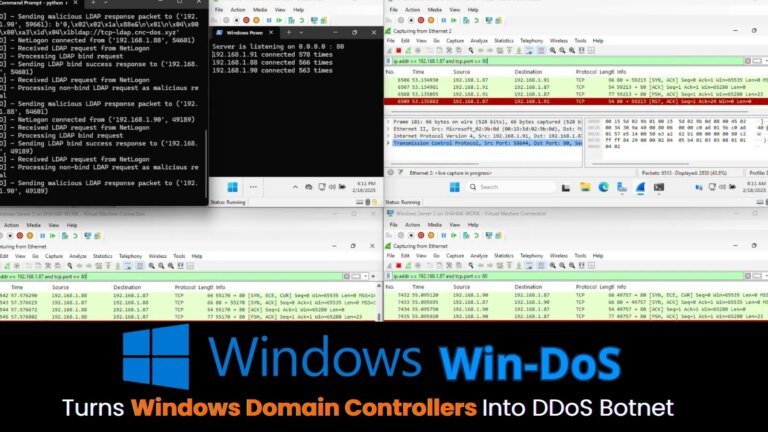
Microsoft has introduced a Common Vulnerabilities and Exposures (CVE) reporting capability within Windows Autopatch to improve security for IT teams. This tool provides an overview of Windows vulnerabilities addressed in recent updates, enabling device-specific tracking. Key features of the CVE report include a list of CVEs addressed in the past 90 days, tracking of patch compliance at the device level, links to Knowledge Base articles, filtering options, and near real-time updates. Administrators can access the CVEs report by navigating to the Microsoft Intune admin center and selecting the appropriate reports. The report includes CVE identifiers, severity scores, exploitation status, and details on devices needing updates. Organizations can enhance their response to vulnerabilities by utilizing various strategies, such as the Windows Autopatch update readiness feature and targeted fixes with the Security Copilot Vulnerability Remediation Agent.