In late October 2024, the developers of the qBittorrent project released version 5.0.1, addressing a long-standing issue related to improper validation of SSL/TLS certificates that had persisted for 14 years. This update effectively mitigates a vulnerability that had exposed users to man-in-the-middle (MitM) attacks.
Details of the Vulnerability
Experts from Sharp Security clarified that the vulnerability in qBittorrent 5.0.1 allowed for remote code execution due to the application’s failure to verify SSL/TLS certificates within the DownloadManager component, which oversees downloads throughout the application. This flaw was first documented in a project commit dated April 6, 2010.
The core issue stemmed from the fact that since 2010, qBittorrent had accepted any certificate, including fraudulent or unauthorized ones. This oversight enabled malicious actors to execute MitM attacks, manipulating network traffic undetected. As noted by a security researcher, “The DownloadManager class in qBittorrent ignored all SSL certificate verification errors that occurred across all platforms for 14 years and 6 months, starting from the commit on April 6, 2010. The default behavior was altered to enforce verification on October 12, 2024, culminating in the release of version 5.0.1.”
SSL certificates are crucial for ensuring that users connect securely to legitimate servers by verifying that the server’s certificate is authentic and issued by a trusted certificate authority (CA). If this verification is bypassed, any server masquerading as legitimate can intercept, alter, or inject data into the data stream, and qBittorrent would unwittingly trust this data.
Identified Risks
Sharp Security highlighted four primary risks associated with this vulnerability:
- When Python is unavailable on Windows, qBittorrent prompts users to install it via a hardcoded URL pointing to the Python executable. Without certificate verification, an attacker intercepting this request could substitute the response URL with a malicious Python installer capable of executing remote code.
- qBittorrent checks for updates by extracting XML from a hardcoded URL and parsing the links for downloading new versions. In the absence of SSL verification, an attacker could replace the update link with a malicious one, tricking users into downloading harmful content.
- The DownloadManager in qBittorrent is also utilized for RSS feeds, allowing attackers to intercept and modify the content of these feeds, potentially inserting malicious URLs disguised as safe torrent links.
- qBittorrent automatically downloads a compressed GeoIP database from a hardcoded URL and unpacks it, creating opportunities for exploitation through potential buffer overflow vulnerabilities using files obtained from a counterfeit server.
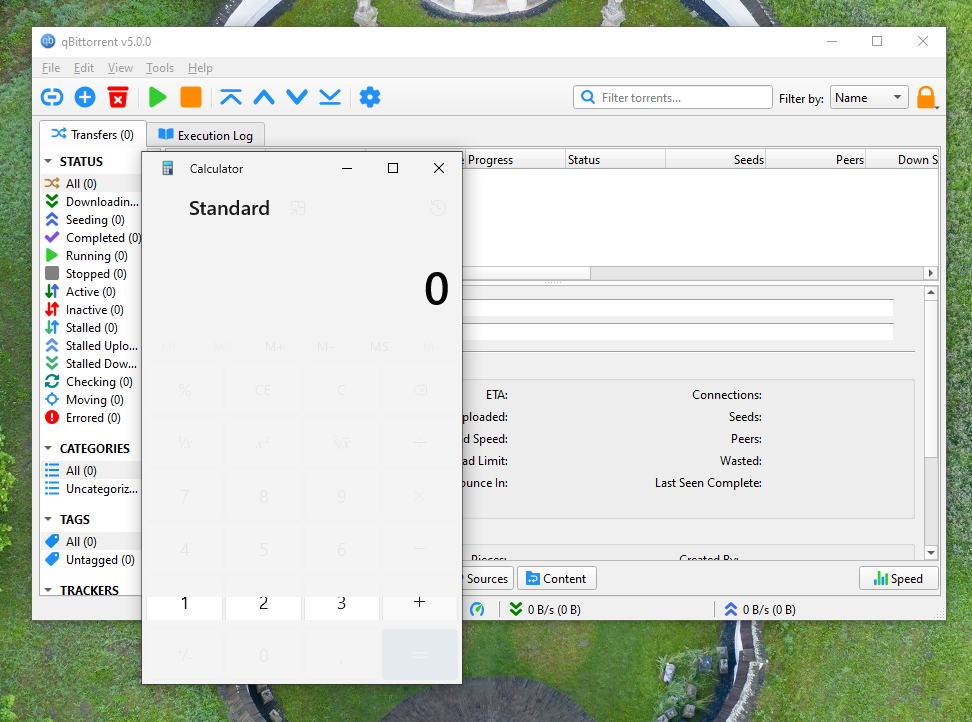
An example of remote execution of the system application “Calculator” through the exploitation of this vulnerability in qBittorrent. Researchers from Sharp Security noted that while MitM attacks are often perceived as unlikely, they may be more prevalent in certain regions with heightened malicious network activity.
In late September 2024, the qBittorrent 5.0 client was released, developed using the Qt toolkit and positioned as an open-source alternative to µTorrent in terms of interface and functionality. The project’s source code is written in C++ and JavaScript and is available on GitHub under the GPLv2+ license. Builds of qBittorrent can be found for Linux, Windows, and macOS. The previous major release, qBittorrent 4.0, was launched in November 2017.