Aug 19, 2024Ravie LakshmananMalvertising / Cybercrime
Surge in Malware Infections Linked to Malvertising Campaigns
Recent findings from cybersecurity researchers highlight a significant increase in malware infections attributed to malvertising campaigns that deploy a loader known as FakeBat. The Mandiant Managed Defense team has provided insight into these opportunistic attacks, which specifically target users in search of widely-used business software.
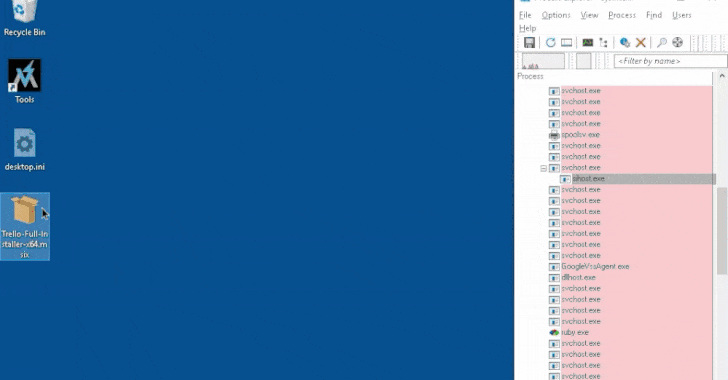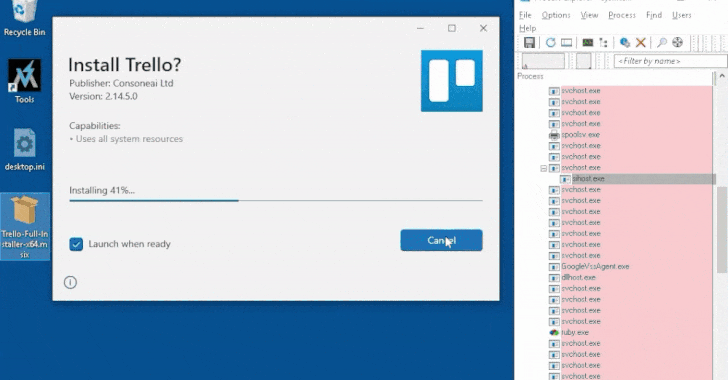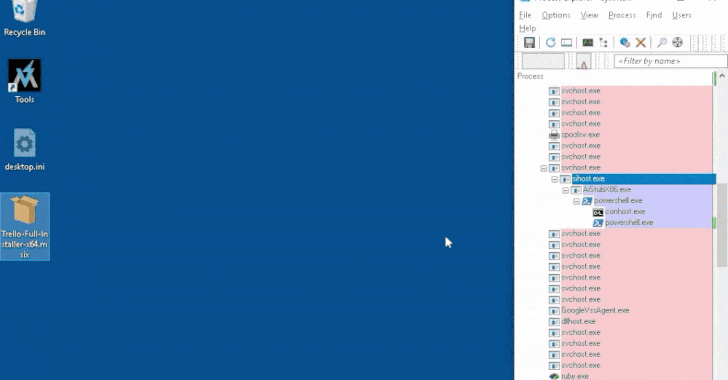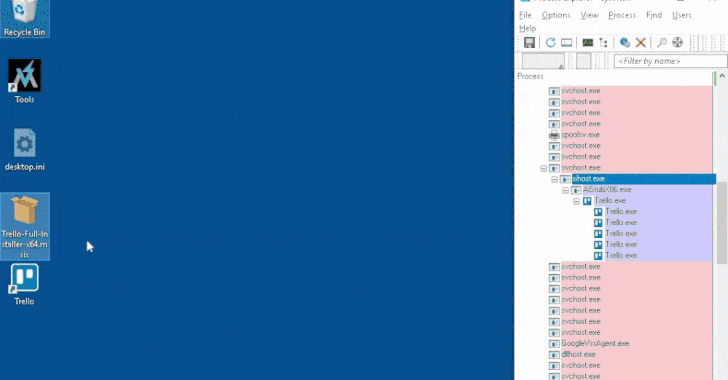
According to the report, the infection process involves a trojanized MSIX installer that executes a PowerShell script to retrieve a secondary payload. FakeBat, also recognized as EugenLoader and PaykLoader, is associated with a threat actor identified as Eugenfest. The Google-owned threat intelligence team has classified this malware under the name NUMOZYLOD and has linked it to the Malware-as-a-Service (MaaS) operation known as UNC4536.
Attack chains utilizing this loader malware employ drive-by download techniques, steering unsuspecting users toward counterfeit sites that mimic legitimate software platforms. These sites host compromised MSI installers, leading to the installation of various malware families, including IcedID, RedLine Stealer, Lumma Stealer, SectopRAT (also referred to as ArechClient2), and Carbanak, which is tied to the notorious FIN7 cybercrime group.
Mandiant elaborates on UNC4536’s strategy, stating, “The group leverages malvertising to distribute trojanized MSIX installers disguised as popular software like Brave, KeePass, Notion, Steam, and Zoom.” These deceptive installers are hosted on websites designed to closely resemble authentic software distribution sites, enticing users into downloading them.
What sets this attack apart is the use of MSIX installers that can execute a script prior to launching the main application, utilizing a configuration known as startScript. Essentially, UNC4536 operates as a malware distributor, with FakeBat serving as a conduit for delivering subsequent payloads to their business associates, including the FIN7 group.
Mandiant further notes that NUMOZYLOD collects various system information, such as operating system details, domain membership, and installed antivirus products. In certain variants, it also captures the public IPv4 and IPv6 addresses of the host, transmitting this data to its command and control (C2) server. Additionally, it creates a shortcut (.lnk) in the StartUp folder to ensure persistence.
This disclosure follows closely on the heels of Mandiant’s previous report detailing the attack lifecycle of another malware downloader known as EMPTYSPACE (also referred to as BrokerLoader or Vetta Loader). This particular malware has been employed by a financially motivated threat cluster, dubbed UNC4990, to facilitate data exfiltration and cryptojacking activities targeting entities in Italy.