Exploiting Novel Attack Technique with GrimResource
Threat actors have been identified exploiting a new attack technique using specially crafted management saved console (MSC) files to achieve full code execution through Microsoft Management Console (MMC) while evading security defenses.
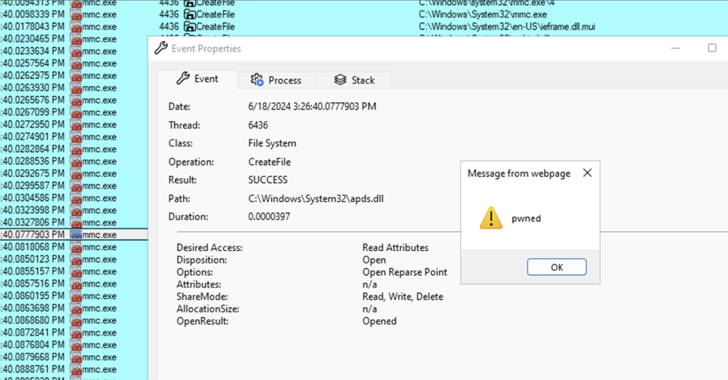
The approach, codenamed GrimResource by Elastic Security Labs, was discovered after an artifact (“sccm-updater.msc”) was uploaded to the VirusTotal malware scanning platform on June 6, 2024.
According to the company, when a malicious console file is imported, a vulnerability in one of the MMC libraries can allow adversary code to run, potentially leading to malware execution. Attackers can combine this technique with DotNetToJScript to achieve arbitrary code execution, opening the door to unauthorized access and system takeover.
This method of using uncommon file types as a malware distribution vector is a creative attempt by adversaries to bypass security measures put in place by Microsoft, such as disabling macros in Office files downloaded from the internet.
The GrimResource technique exploits a cross-site scripting (XSS) flaw in the apds.dll library to execute JavaScript code within the context of MMC. Despite being reported to Microsoft and Adobe in 2018, the XSS flaw remains unpatched, allowing for the execution of JavaScript code when a malicious MSC file is opened using MMC.
Not only does this technique bypass ActiveX warnings, but it can also be combined with DotNetToJScript to achieve arbitrary code execution. The analyzed sample utilizes this approach to launch a .NET loader component called PASTALOADER, ultimately facilitating the deployment of Cobalt Strike.
Security researchers Joe Desimone and Samir Bousseaden noted that following Microsoft’s default disabling of Office macros for internet-sourced documents, alternative infection vectors like JavaScript, MSI files, LNK objects, and ISOs have gained popularity. However, these methods are closely monitored by defenders and are more likely to be detected, prompting attackers to develop new techniques like executing arbitrary code in Microsoft Management Console using crafted MSC files.