In a recent wave of cyber threats, many GitHub users found themselves targeted by a sophisticated phishing email that mimicked communications from GitHub’s security team. The email warned recipients of critical vulnerabilities in their repositories, urging them to visit a dubious link for further details. The message read: “Hey there! We have detected a security vulnerability in your repository. Please contact us at https://github-scanner[.]com to get more information on how to fix this issue.”
Unraveling the Phishing Scheme
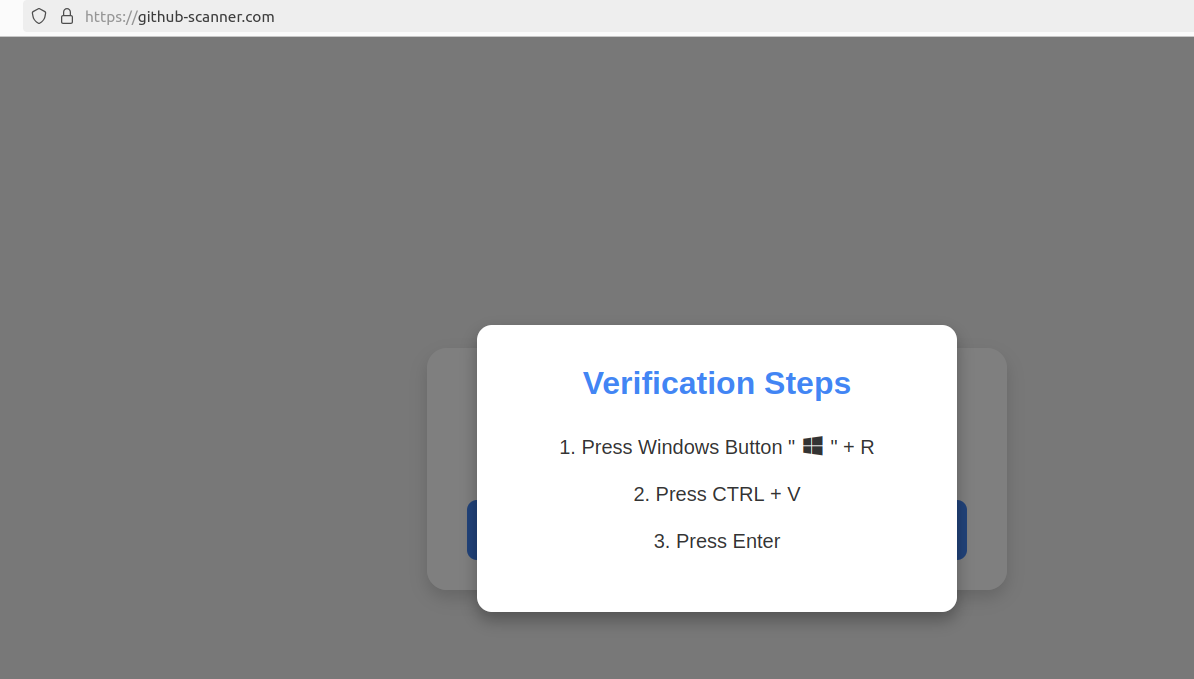
Upon clicking the link, users were directed to a webpage that employed a deceptive CAPTCHA, designed to differentiate between humans and bots. This particular scheme required users to engage in a series of keyboard actions that inadvertently initiated a download of password-stealing malware.
The first step in this elaborate ruse involved pressing the Windows key in conjunction with the letter “R,” which opens the Windows “Run” prompt. This prompt can execute any program already installed on the system, setting the stage for the malware to infiltrate the user’s device. The second step instructed users to press “CTRL” and “V” simultaneously, pasting malicious code from the site’s virtual clipboard. Finally, pressing the “Enter” key executed a PowerShell command that fetched a harmful file named “l6e.exe” from the phishing site.
According to an analysis by the malware scanning service Virustotal.com, this file, known as Lumma Stealer, is designed to extract any stored credentials from the victim’s computer. While seasoned programmers may recognize the red flags in this phishing attempt, the approach could easily ensnare less tech-savvy individuals who may not be familiar with the implications of these commands.
As the digital landscape evolves, so too do the tactics employed by cybercriminals. This phishing campaign illustrates a growing trend that could potentially exploit the vulnerabilities of everyday users. It raises the question of whether there should be more stringent measures in place to protect those who may not fully understand the risks associated with such scams.
Despite the potential dangers, Microsoft advises against disabling PowerShell entirely, as it plays a crucial role in the functionality of various system processes. Modifying PowerShell settings requires navigating sensitive areas of the Windows registry, a task that can be daunting even for experienced users.
In light of these developments, it may be prudent to share this information with less tech-savvy Windows users in your circle. As phishing schemes continue to evolve, awareness and education remain key defenses against these increasingly creative attacks.