Microsoft is revisiting its Recall feature for Copilot+ on Windows PCs, following a tumultuous initial rollout that faced significant backlash from security experts and testers during the summer months. The original iteration of Recall was criticized for its approach to user data, as it captured screenshots and text through optical character recognition (OCR), storing this information unencrypted on local disks. This raised alarms about potential unauthorized access by other users on the same device or by remote attackers.
Initially unveiled in late May, the feature was set to debut on new PCs by June 18. However, just days before its launch, Microsoft opted to postpone the release indefinitely to address security concerns and ensure proper testing through the Windows Insider program.
More secure, also optional
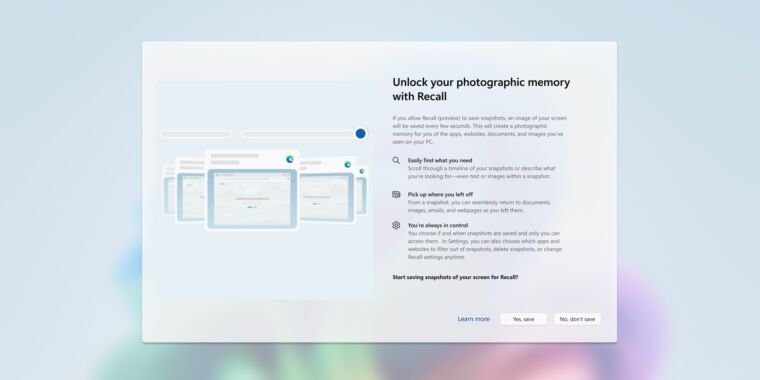
In a recent update, Microsoft provided a comprehensive overview of the enhancements made to Recall’s security framework, as detailed by David Weston, Vice President of Enterprise and OS Security. The revised feature will now be opt-in by default, requiring users to actively choose to enable it. Additionally, access to Recall data will necessitate re-authentication through Windows Hello, and all locally stored Recall data will be safeguarded with enhanced encryption protocols.
To further alleviate user concerns, Microsoft has introduced a mechanism allowing users to completely remove Recall from their systems via the “optional features” settings in Windows. This marks a shift from earlier claims that such a removal option was merely a bug. The company has also clarified how data protection will be implemented: all Recall data, including snapshots and associated information, will be encrypted at rest, with encryption keys securely stored in the device’s Trusted Platform Module (TPM). Recall will only operate when BitLocker or Device Encryption is fully enabled, alongside requirements for Virtualization-Based Security (VBS) and Hypervisor-Protected Code Integrity (HVCI). These features, often disabled for gaming performance, are now essential for Recall’s functionality.
The new architecture places Recall within a VBS enclave, creating a secure environment that isolates and protects data in memory from other system processes. Weston emphasized that this enclave acts as a “locked box,” accessible only after user permission is granted through Windows Hello. Furthermore, only Microsoft-signed code can execute within these enclaves, significantly reducing the risk of data exposure to malware or unauthorized applications. Additional security measures, such as rate-limiting and anti-hammering protocols, have also been integrated into this version of Recall.
Users will be required to re-authenticate with Windows Hello each time they access Recall, with biometric authentication being the primary method. A Windows Hello PIN can serve as a fallback option, configured only after Recall is enabled. The decryption of Recall data occurs briefly during access, with periodic re-authorization needed to maintain security. The encryption keys are cryptographically bound to the user’s identity, addressing the vulnerabilities present in the original version that allowed easy access to Recall data by other users on the same PC.
Microsoft has also included user-configurable settings to limit the data Recall collects. These settings allow users to manage disk space usage, retention periods for snapshots, and exclusions for specific applications and websites. A new feature aimed at filtering sensitive content seeks to minimize the storage of passwords, national ID numbers, and credit card information, leveraging Microsoft Purview Information Protection technology.
While Microsoft asserts that the new Recall has undergone rigorous audits, including design reviews and penetration testing by both internal teams and third-party security vendors, questions remain regarding the initial oversight that allowed the original version to launch without adequate security measures. The company has yet to respond to inquiries about the internal processes that led to this lapse.
Recall is still just for new PCs
It is important to note that Recall will only be available on a limited number of Windows PCs that meet the stringent requirements of the Copilot+ program. Eligible devices must feature at least 16GB of RAM, 256GB of storage, and a neural processing unit (NPU) capable of executing a minimum of 40 trillion operations per second (TOPS). Currently, this includes select Arm Windows PCs equipped with Snapdragon X Plus or X Elite chips, as well as x86 PCs powered by Intel’s Core Ultra 200V-series or AMD’s Ryzen AI 300-series chips. Notably, no desktop processors meeting these specifications have been released as of yet.
While Microsoft has not provided a specific timeline for the reintroduction of Recall, it previously indicated that the feature would begin rolling out to Windows Insiders in October.